HTB – Beep – FH: LFI
Foot-hold: Local File Inclusion
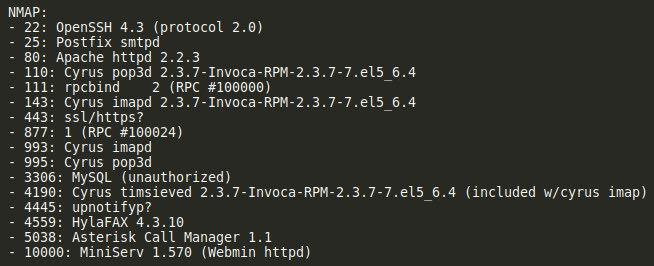
For the Beep box, there were several ports found with NMAP. Some looked like mail servers, and others for MySQL and other things. So I explored around for each of them.
Found login page via https://10.10.10.7/
Port 80 redirects to this…

I didn’t know what the Miniserv was on port 10000, but I figured I’d give that a try as well. It didn’t work unless I put the https in front of the URL.
Next, I went ahead and tried a suggestsploit on each of the items found on the ports. There were quite a few of them, so I concentrated on things that stood out to me. Hylafax. MiniServ, Cyrus, imapd, and timsieved. Most of them had no results, but I got some hits from imapd and webmin (found that below).
The text file from the imapd said that I could execute remote commands through a URL:
http://target.host/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd
That redirected me to a login for webmin… which is why I ended up doing a searchsploit on it.
Found a login page at https://10.10.10.7:10000/session_login.cgi
Here’s where I was stumped… although I found some interesting things, I didn’t have anything that would get me into the machine. As is fairly normal, what I realized is that I hadn’t enumerated the very thing that I first found, the actual webpage that popped up. It was clearly an installation of something called Elastix. So back to Google!
Elastix: https://www.elastix.org/
This appears to be a PBX for VoIP phones. I’ve built quite a few FreePBX VoIP systems, so I felt immediately familiar with the environment; but how could I get into the box?
Now it’s onto the standard Google search term… just put exploit after whatever server name you found.
Found two exploits from exploit-db
Remote Code Execution – https://www.exploit-db.com/exploits/18650
CVE 2012-4869
Local File Inclusion – https://www.exploit-db.com/exploits/37637
CVE N/A
First, try the Remote Code Execution CVE… I would have loved for this one to work. Usually when they do, you can get a reverse shell on your listener right away, but the results were not worth chasing.
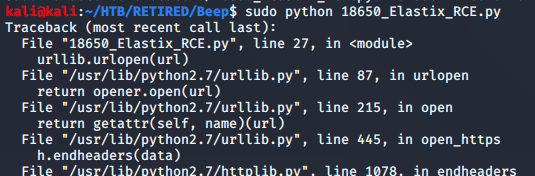
Got the standard error messages when a python scrip doesn’t work. I tried python2 and python3 as well… but it didn’t work. With another possible exploit in the queue, it was time to move on. If I get to a brick wall, I can always come back to this to try and make it work.
Time to move on to the other exploit. It looks like simply trying out the URL inside of the exploit file is the key. There was quite a bit of other text on the exploit page, but I didn’t see any way to run a script with it. So a copy/paste of the suggested URL revealed this…
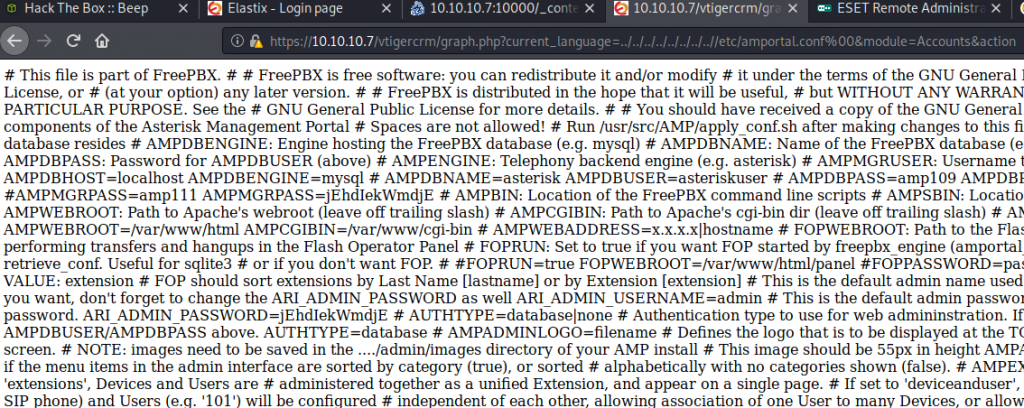
The exploit was a Local File Inclusion which is basically traversing the server to get to folders and files that should not be accessible. You can see that in the URL with ../../../../, etc.
This is normal, and never daunting. I’m commonly finding huge texts like this and configuring them via CLI tools. In this case, I would use sed. As you can probably see in the picture, there are quite a few comment characters. I can use these to create a new line after each. Hopefully, it will reveal something…. and it did.$ sed 's/#/&\n/g' elastix_LFI.txt
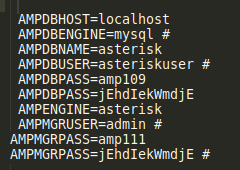
Okay… now let’s give them a try. I used the first page that popped up (picture above) to try out all the things. There were a couple users, and quite a few passwords there. As an easy target, I tried out ‘admin’ first, and just started from the top for the passwords; of course, it was the last password on the list that worked… but who cares… it worked!
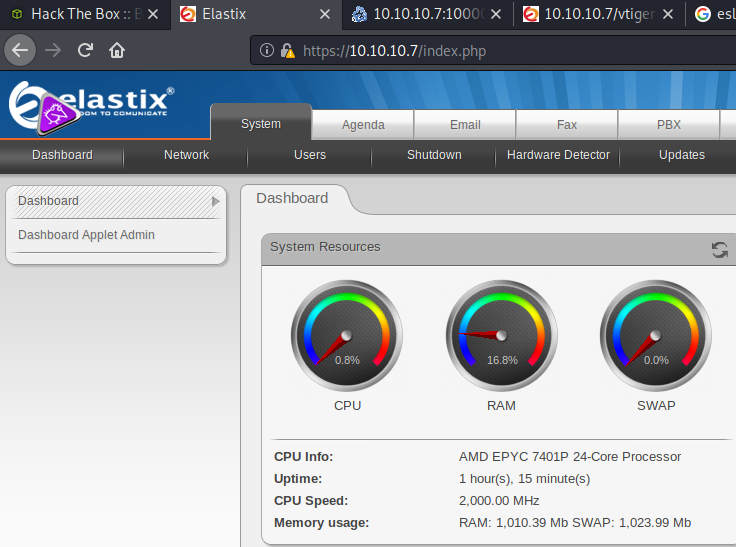
So now what?!? I could play around with this dashboard, I guess, but how would I be able to get into the box? A file upload, perhaps? I think a better way is to see if other logon methods would work. So let’s try some SSH.
The SSH attempt was a fail, but the error message that it gave me was something I hadn’t seen before. Back to Google!
Google: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
https://www.openssh.com/legacy.html
Excerpt:
“In this case, the client and server were unable to agree on the key exchange algorithm. The server offered only a single method diffie-hellman-group1-sha1. OpenSSH supports this method, but does not enable it by default because it is weak and within theoretical range of the so-called Logjam attack.”
This gave a command: ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 user@legacyhost
Let’s give it a try!
I tried each of the passwords above with the user name admin, and the username root. Admin did nothing, but ROOT!!! Yep, that was it! PWND!
