HTB – Bank – FH: DNS / File Upload
The Bank box was the first time I ran into virtual hosts on a web server. Till now, I’ve been able to discover all of the directories with a simple dirb or gobuster scan… this time was very different.
The NMAP scan showed only a few ports open. 22, 53, and 80. I always bypass 22 because there are rarely SSH exploits that go quick, so it was on to the other two ports. Interestingly, they had DNS running on port 53 and the description was ICS BIND. Bind is the Berkeley Internet Name Domain, and ISC bind can run in a large number of Linux environments. In this case, it was used to map to folders that didn’t show on an IP address scan of the machine.
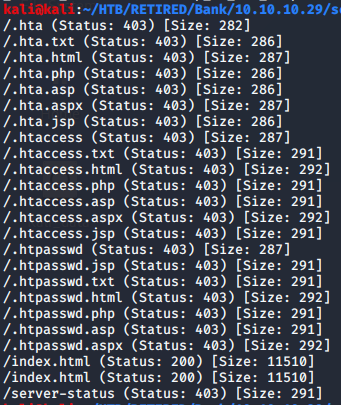
The regular IP scan of the machine (10.10.10.29) showed quite a few hidden files, and the main index file used to show the Ubuntu web server page. I visited a few of these just to see if I could find something interesting, but nothing was useful.
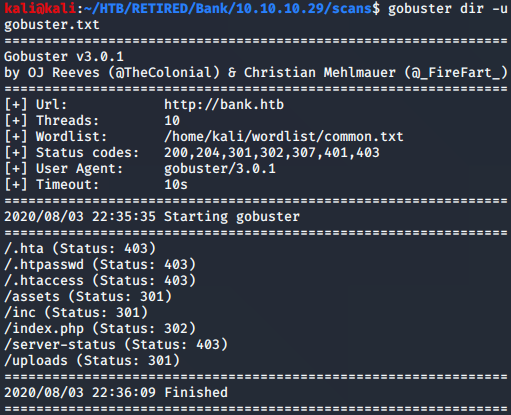
With the help of Google, I figured out the DNS name of this machine (it was obvious at this point) and added it to my /etc/hosts file. When I ran the gobuster search again, the results were remarkably different.
Going to http://bank.htb now revealed a logon page instead of the ubuntu web server splash page.
The first scan that I ran was using the dirb program’s common.txt file which is limited in results. I always start with that one because it is quite a bit smaller and can reveal things faster. After trying out a couple of the new directories that I found, I came to another wall where access was forbidden.
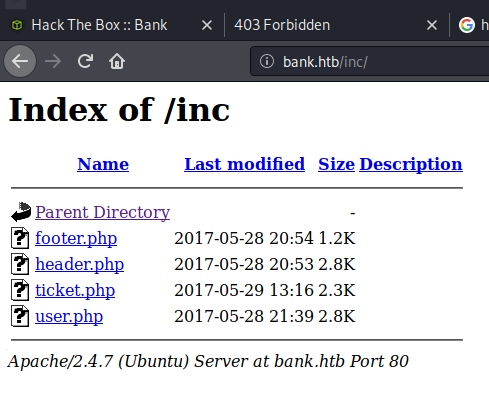
Because of this, I ran a new gobuster scan, but used the medium sized directory file. It takes quite a bit longer, but yields results that are usually useful. In this case, it found a folder that was absolutely crucial to getting into this box. The directory was /balance-transfer, and it had hundreds of files in it. Almost all of them were encrypted.
The .acc files were readable, but the user account data was what was encrypted. I could have tried some hash cracking, but truthfully, I wouldn’t know where to start. I’d have to match up these hashes somehow, and figure out emails addresses and passwords. There had to be an easier way!
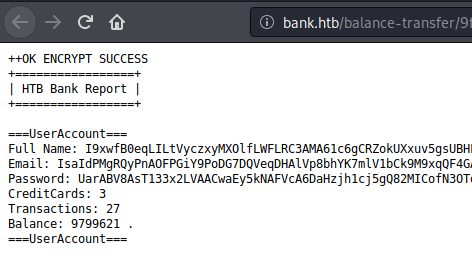
The easier was wasn’t too difficult to find. I noticed that most of the files were around the size of 584. When I was using BurpSuite on another machine, I used a technique to watch responses from repeater and look for noticeably different sizes. I the case of the /balance-transfer folder, I just did a size sort and saw that there was only one file that was about half the size of the others. Instead of clicking on hundreds of these things, this narrows it down to only one.
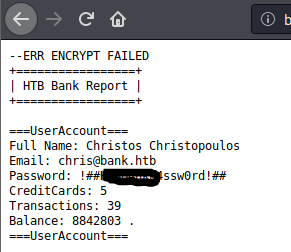
And there’s the weakness! Because of only one unencrypted file, I now can see an email address and password that I can try in the bank.htb login URL.
There weren’t too many options after logging in; there were basically two. There was a summary page, and a support page. The summary page didn’t offer anything useful since I’m not out to own the guy’s credit card data, but it did offer something better than credit cards…
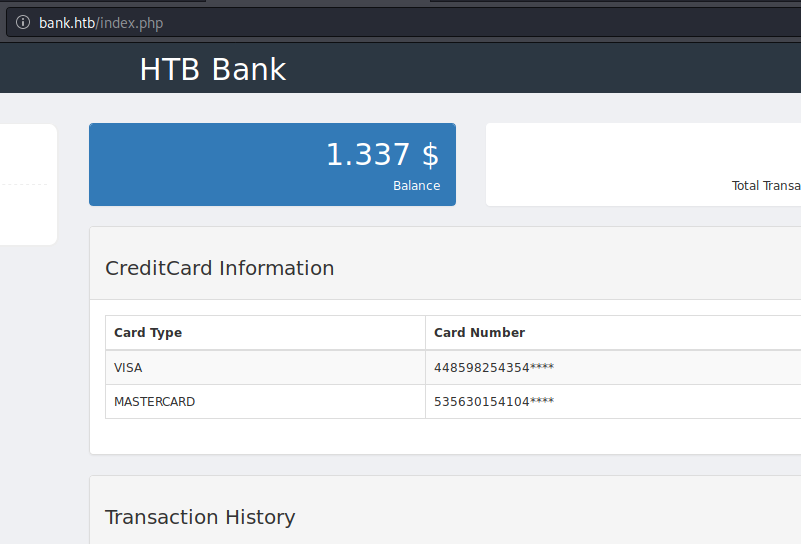
… an UPLOAD section. At this point after hacking several HTB machines, a pattern emerges. Find a web portal with an upload, and use it to access a reverse shell. In the case of Bank, I just got there.
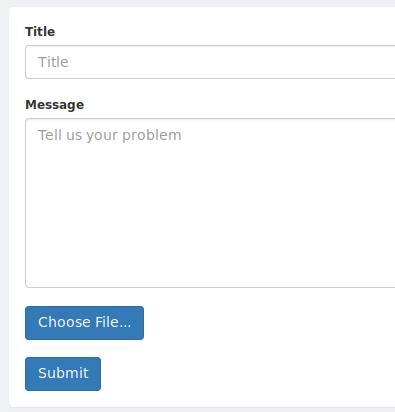
The first thing I tried was a php file… standard. It didn’t work. After peaking at the source code for the page, I found a comment that said that .htb files are trusted. So it could be as simple as changing the filename to shell.htb.
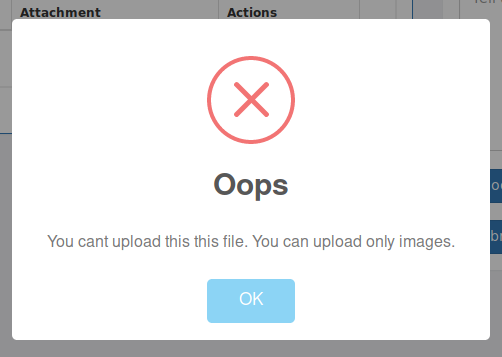
Perfect, it worked. It was the same file downloaded from my favorite php reverse shell site, but I changed the name to shell.htb.
After uploading the file, it showed up as a support ticket. Clicking on the ‘Click Here’ button would activate the reverse shell and give me access to the box.
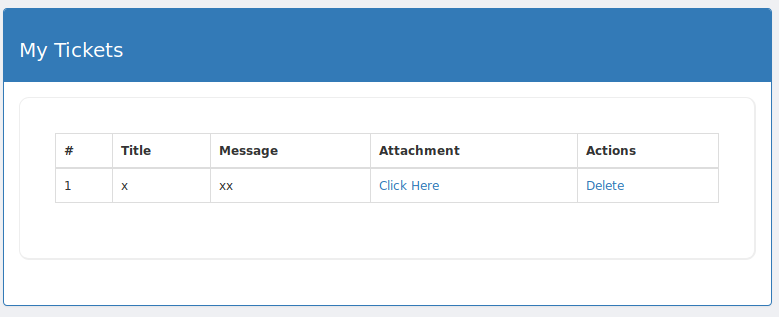
With a netcat listener at the ready, I went ahead and clicked on the button to make the magic happen. There I was as user www-data (web user). This is where many of the boxes have left me, and it’s great because I can practice the privilege escalation part of my learning in a very standard style.
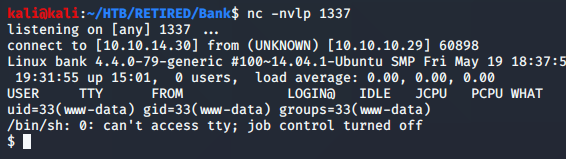
Per normal, I went ahead and tried to make it a TTY shell. My standard one-liner worked just fine for this.