The Petting Zoo – CTF
DC702 CTF FOR CREECH AFB
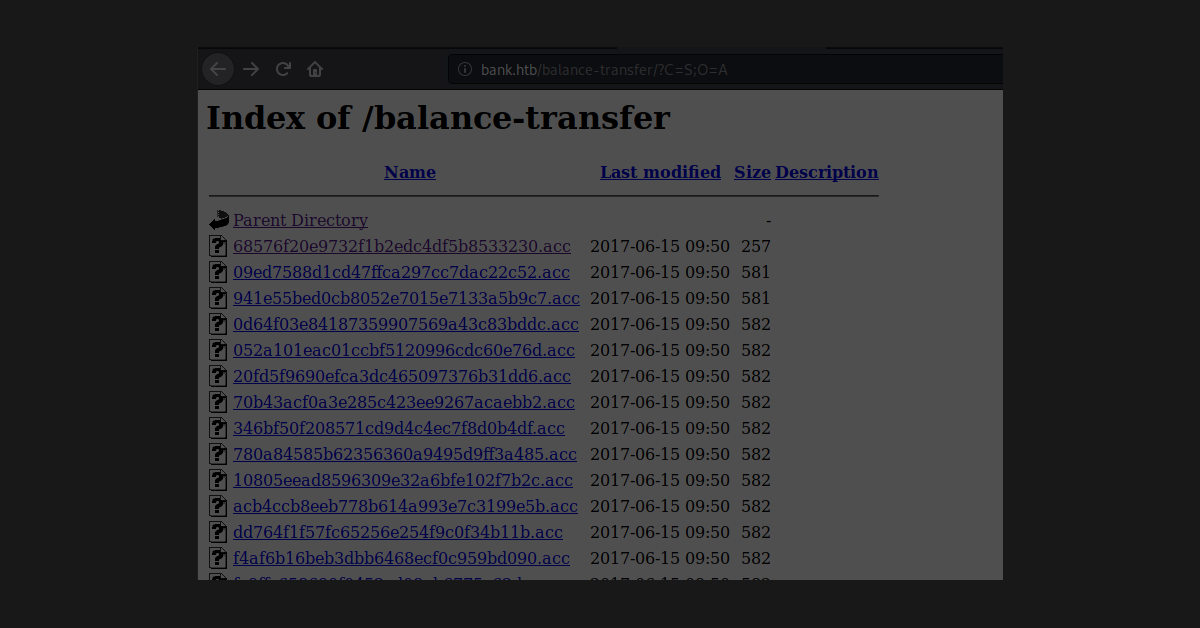
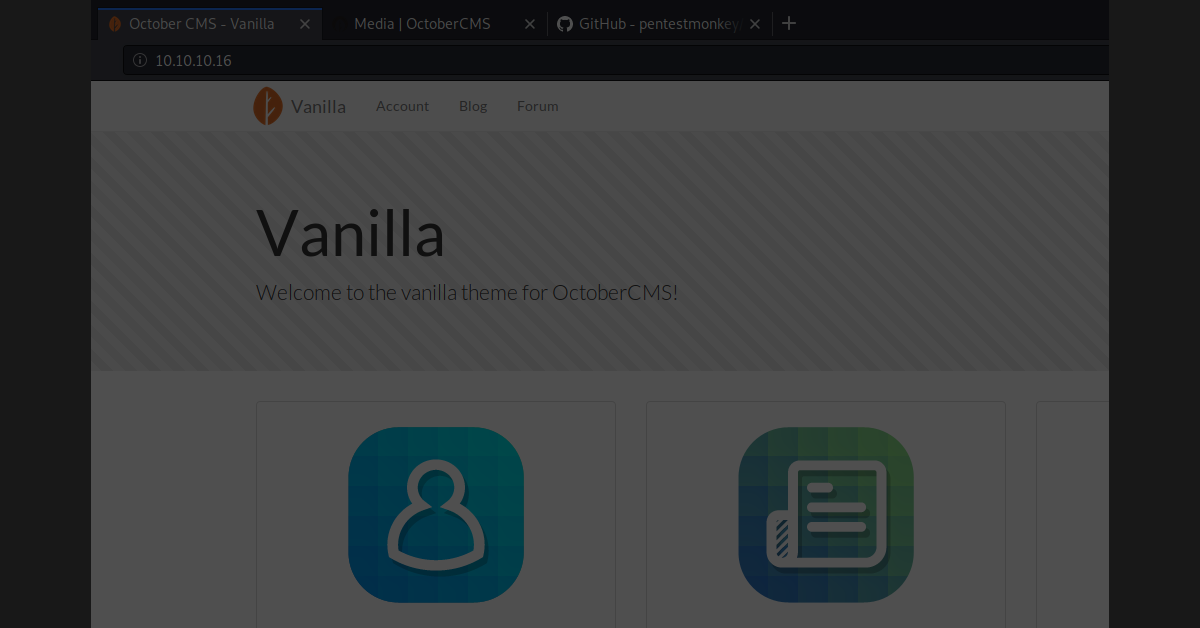
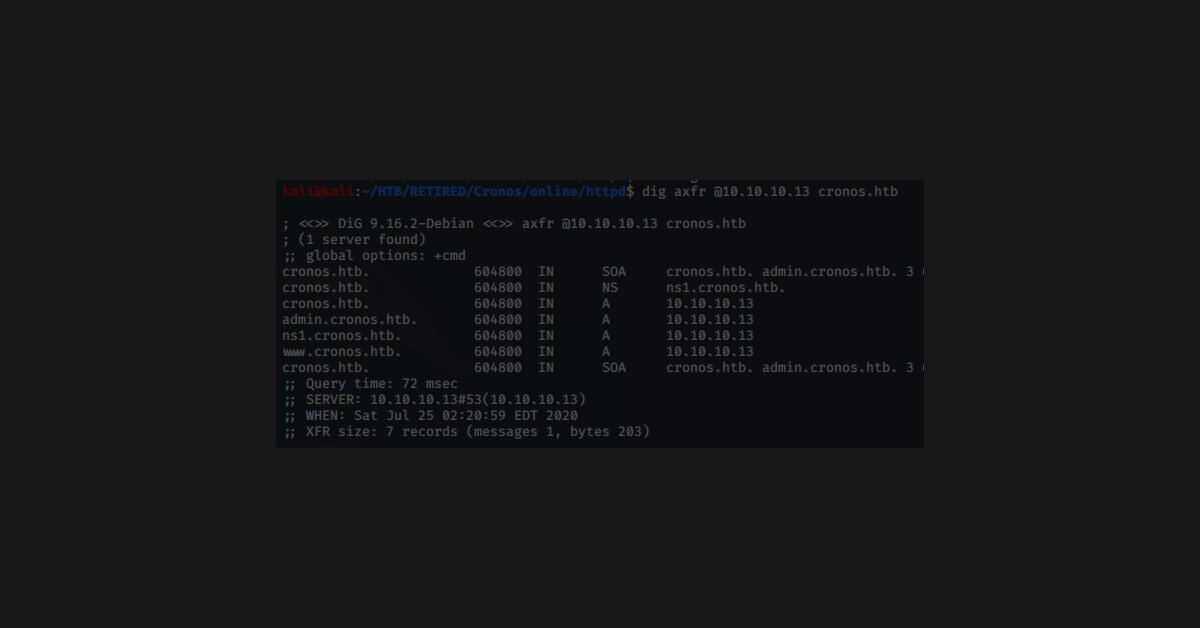
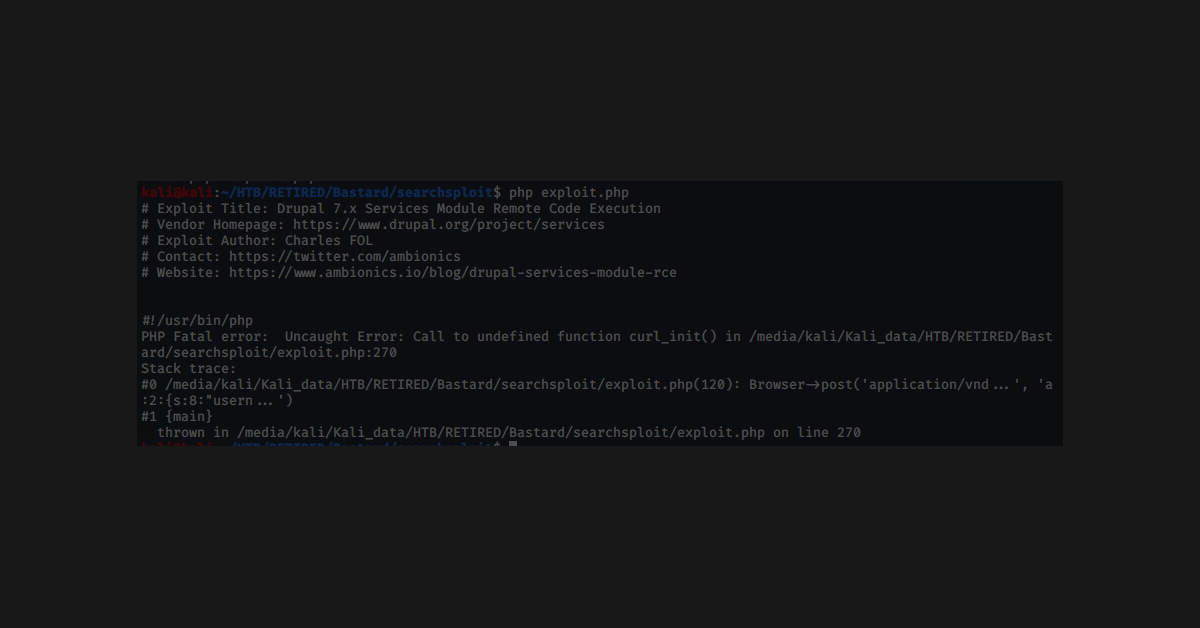
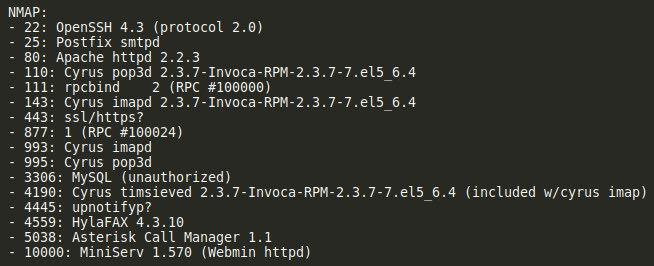
The Las Vegas local hacking group, DC702, will be hosting a Capture The Flag (CTF) event at Creech Air Force Base to promote cyber education. Presenters include intelegence professionals who will describe worldly hacks and the orginizations from which they originate. This post describes the thoughtful process that went into creating the various challenes that will be used for the challenges.
Plesae note that our experts use this daily, and this post is intended to give its audience a basic understanding of Docker and how systems can be developed using it.