HTB – Beep – FH: LFI
Foot-hold: Local File Inclusion
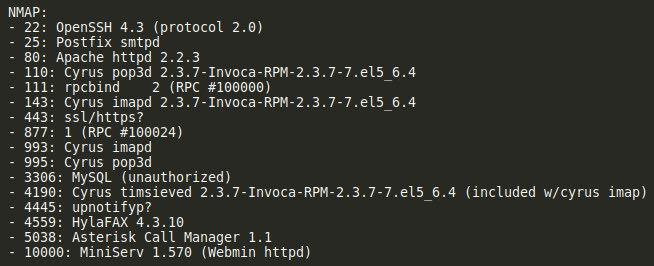
For the Beep box, there were several ports found with NMAP. Some looked like mail servers, and others for MySQL and other things. So I explored around for each of them.
Found login page via https://10.10.10.7/
Port 80 redirects to this…