Status Report 20210801
So it’s been a couple months now, and I’m feeling great about everything that I’ve accomplished. I started out just going after every challenge that I could find, and mostly, I was able to accomplish success.
Shortly into my journey, I realized that I would have much better success with my learning if I were to separate tasks. I have been at the learning game for my entire life, always seeking more knowledge on everything that I do; and I’ve learned a few things about how learning can be best accomplished.
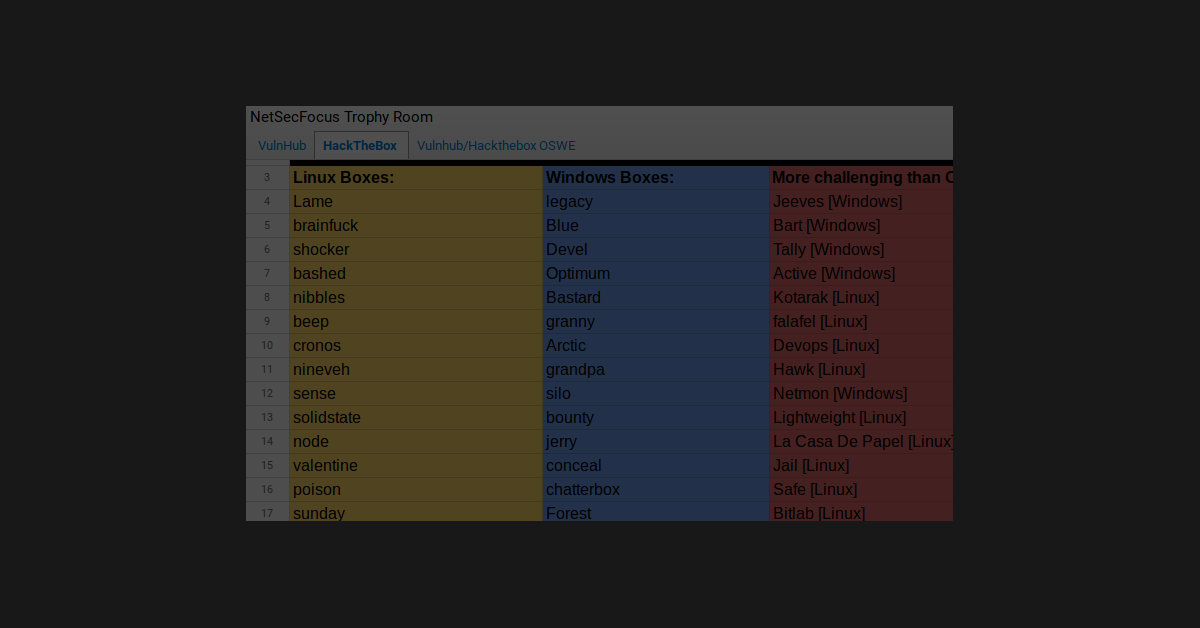
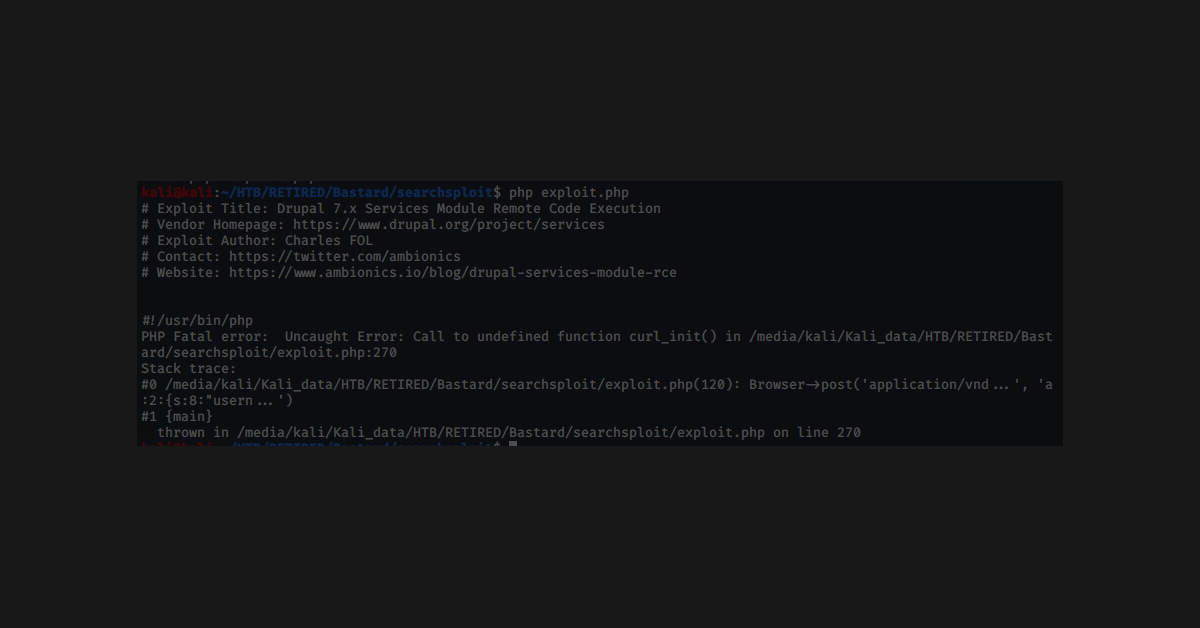
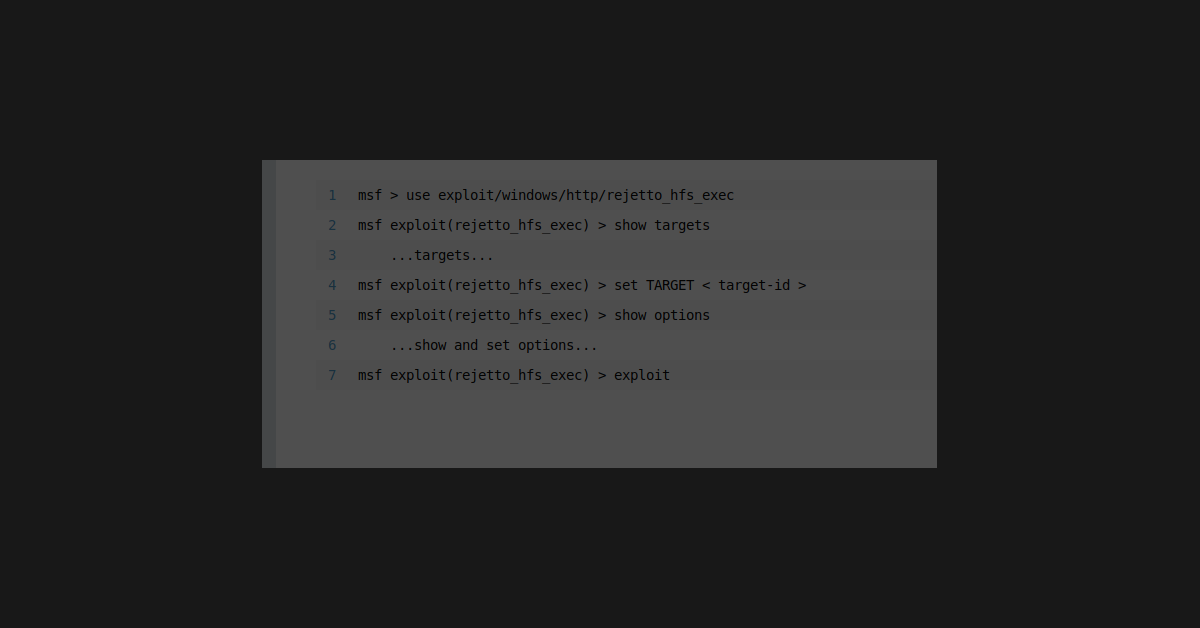
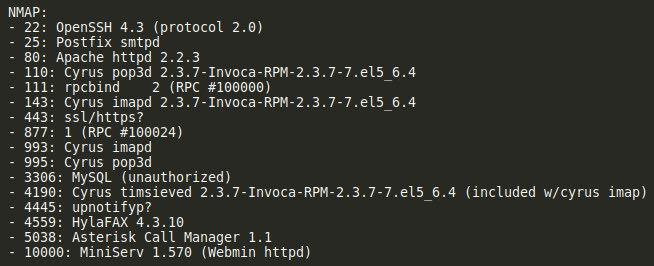
For the task of learning more about hacking, it would be the easy button to go ahead and pwn each box from start to finish. Do the scans, find the foot-hold, get in, then privilege escalate based on some further enumeration. That, however, is not the right answer if you want to get the maximum amount of learning out of each task! Therefore, I separated my learning into compartments that will yield a much greater result.
Continue Reading